Researchers: Gabi Cirlig, Inna Vasilyeva, Vikas Parthasarathy, Dr. Michael Moran, Mikhail Venkov, Michael McNally, Federico Harrington, Adam Sell
Spend more than a couple of hours in any office park and you’re likely to hear a reference to the “80/20 rule”. It’s a concept that says that 80% of the impacts (especially economic impacts) are the result of only 20% of the participants involved in the system. That rule has a name – it’s called the Pareto Principle. And, with our apologies to economist Vilfredo Pareto, the concept lends its name to the latest investigation and disruption carried out by our Satori Threat Intelligence and Research Team.
The PARETO botnet was nearly a million infected Android phones pretending to be millions of people watching ads on smart TVs and other devices. PARETO-associated traffic accounted for an average of 650 million daily bid requests witnessed by HUMAN’s Advertising Integrity solution, the result of 29 Android apps spoofing more than 6,000 Connected TV (CTV) apps. Several of the Android apps were available only through third-party marketplaces. PARETO exploited many organizations and components in the advertising technology ecosystem; references to them within this report do not imply complicity in the operation.
HUMAN’s Satori team also observed a distinct-but-connected operation on Roku: we found a collection of 36 apps on Roku’s Channel Store that received instructions from the same server that was operating nodes in the PARETO botnet. That server, called a command-and-control (C2) server, sends instructions out to all of the phones that have been infected, and those phones then carry out the activity. These Roku apps, in a similar fashion to the Android-based PARETO apps, were spoofing other smart TV and consumer streaming products.
(Note: all of the Android and Roku apps associated with this operation have been removed from official marketplaces. Additionally, information about the organization behind the apps, as well as information about key figures at those organizations, has been turned over to law enforcement.)
Over the course of the scheme, the PARETO operators spoofed:
The PARETO botnet and its adjacent Roku operation are the most sophisticated schemes uncovered in the CTV ecosystem to date. The operators behind the botnet took advantage of the recent shift to digital accelerated by the pandemic by hiding in the noise in order to trick advertisers and technology platforms into believing that ads were being shown on consumer streaming devices.
HUMAN worked closely with our partners in The Human Collective (our recently launched industry-wide initiative for protecting the digital advertising ecosystem from the impacts of fraud)—including The Trade Desk, Omnicom Media Group, and Magnite—and with Google and Roku to disrupt the functional components of PARETO.
The PARETO operation has been sophisticated and evasive over the last year. For each spoofing cycle, as PARETO launched a new disguise for their fake traffic, HUMAN has been forced to detect and continuously innovate techniques to protect our customers. While we’ve been mitigating the impacts of this operation for much of the past year, as PARETO became more aggressive and evasive, we concluded that the time had arrived to take collective action in concert with our partners. We chose to act now to protect the digital advertising ecosystem from the long-term impacts of PARETO.
The majority of fraud in CTV environments is carried out by only a small number of bad actors, hence the operation’s name. It’s the fact that CTV provides massive opportunities for streaming services and brands that makes it attractive to bad actors. Because of the opportunity that CTV offers the advertising community as well as the bad actors, it is incredibly important for the CTV ecosystem and brands to work together through a collectively protected advertising supply chain to recognize, address and fight fraud as quickly as possible.
How It Worked
The core PARETO botnet was nearly one million Android phones strong, and each pretended to be one (or more) consumer streaming products to help the botnet operators cash in on higher prices for CTV advertising. In the thirty days before the takedown, we observed the operation generating an average of 650 million bid requests every day.
We will explore at a high level how the operation worked, how we found it, its level of sophistication, and recommendations for fighting these types of attacks. For cybersecurity professionals looking to learn more about the in-depth tactics in this investigation, check out our technical blog.
Our journey begins with the TopTopSDK. The TopTopSDK is included in several apps we found in the Google Play Store, mostly gaming and basic functionality apps such as the flashlight app—Any Light—shown below. Any Light, claims to be ad-free, and while it didn’t show ads, we discovered the app actually faked ad impressions!
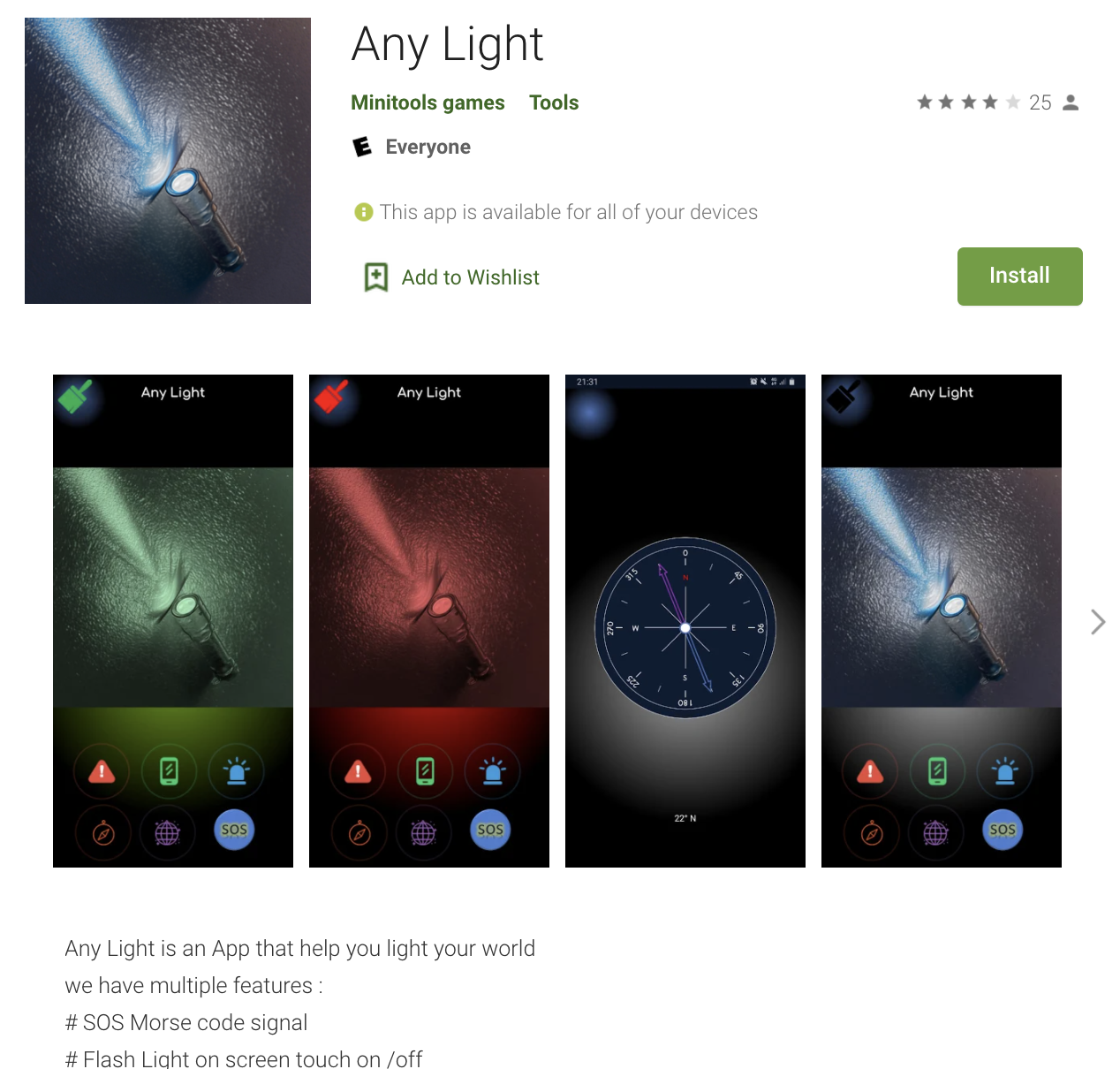
Screenshot of Any Light application in the Play Store
Source: HUMAN’s Satori Threat Intelligence & Research Team
(click on any image in this report to enlarge)
Within the code of the TopTopSDK, we see code that has no place on an ostensibly ad-free app. Notice the ClickURLsService below – why should a flashlight app have URLs to click?
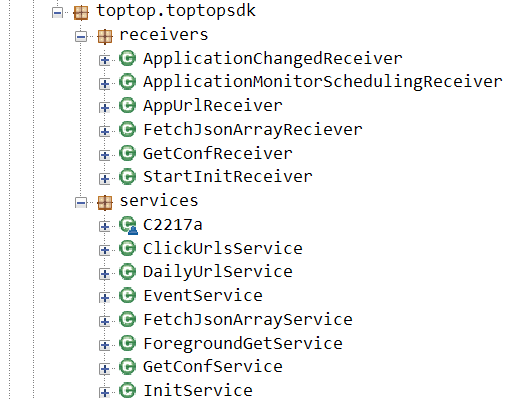
Inside the TopTop SDK
Source: HUMAN’s Satori Threat Intelligence & Research Team
Several of the services above form the mechanism by which Android apps running the TopTop SDK contact a command-and-control (C2) server for instructions. The operators of the botnet obfuscated their work by hiding the URLs of the C2 server within base-64 encoding, as seen below:
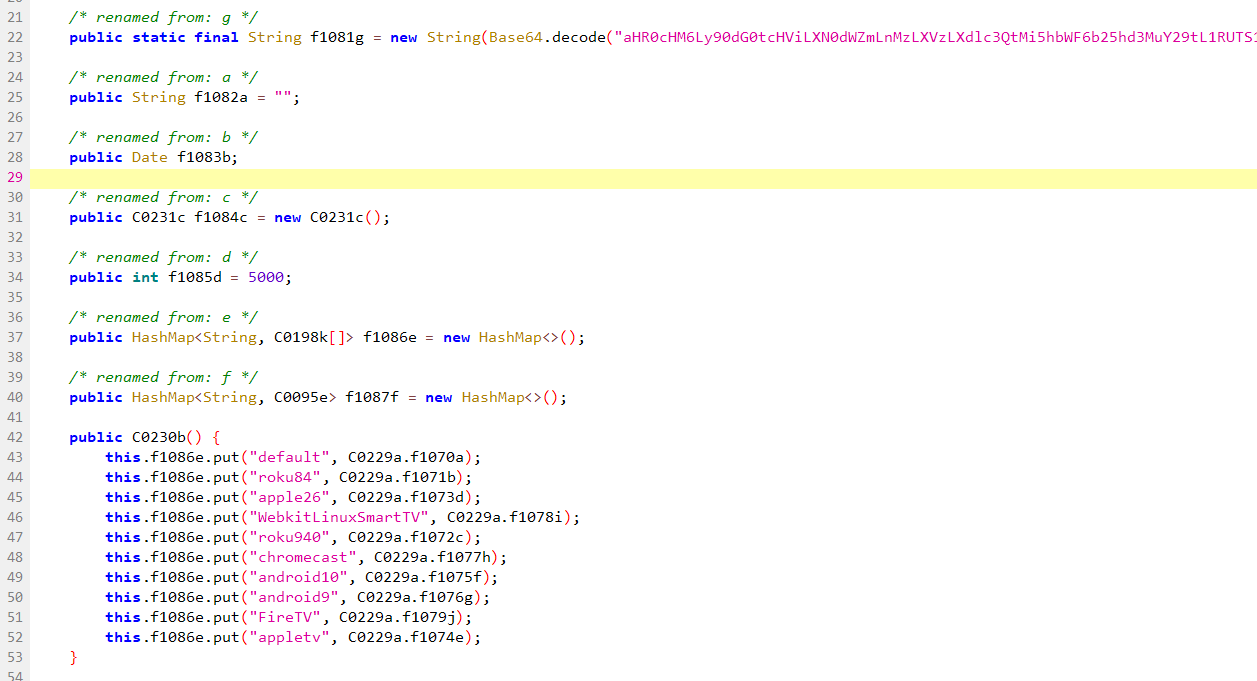
Base64 encoded string
Source: HUMAN’s Satori Threat Intelligence & Research Team
Visiting the decoded URL uncovers a rather cryptic two-field JSON response, an indicator that there’s another layer to decode:
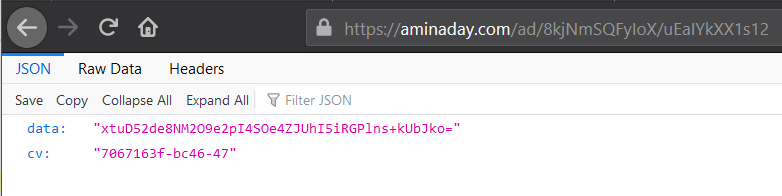
JSON fields
Source: HUMAN’s Satori Threat Intelligence & Research Team
Shifting our attention back to the app code that processes commands from the C2, we can finally see what the C2 server is trying to accomplish:
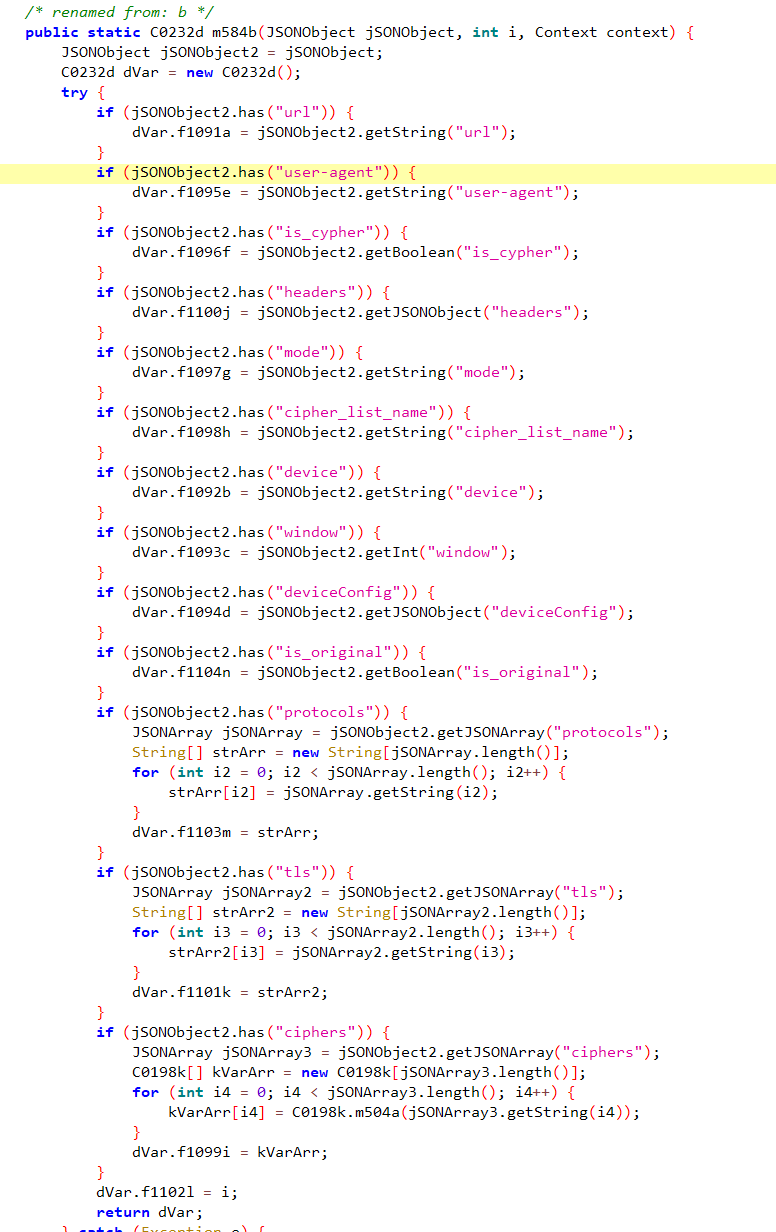
Expected data from C2 in a.c.a.d
Source: HUMAN’s Satori Threat Intelligence & Research Team
The C2 server has the ability to dictate how the Android phone presents itself to ad servers, including device type and device configuration, which make it possible for these nodes in the botnet to pretend to be consumer streaming products:
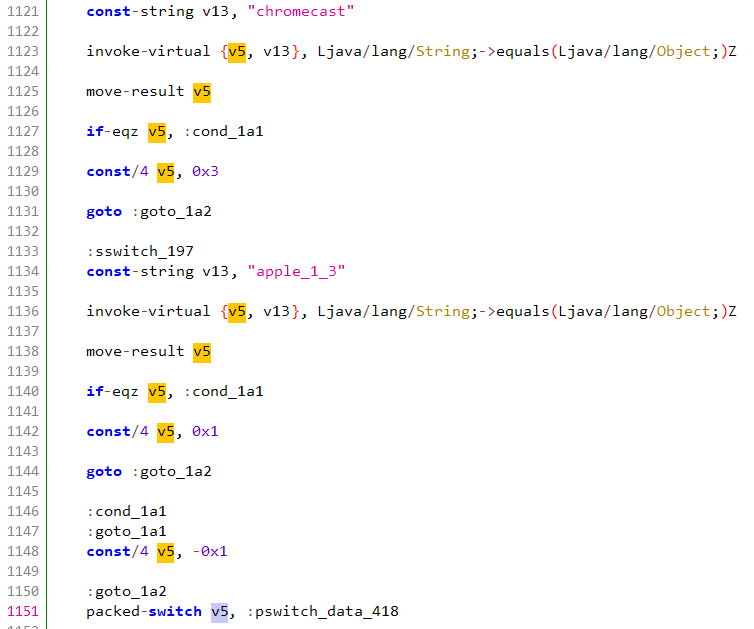
Cipher selection per device
Source: HUMAN’s Satori Threat Intelligence & Research Team
As the code above shows, operators of the botnet went to the trouble of modifying the security parameters of outgoing requests to verification servers— a fundamental of how devices on the internet set up connections—to keep their Android-generated traffic correctly impersonating popular streaming TV products.
In short, TopTop SDK was able to spoof the phone to look like a streaming TV product, telling it to send out fake ad impressions at a higher CPM price which the CTV marketplace commands.
The nearly one million Android phones with apps running the TopTopSDK, acting as nodes of the botnet, would wake up every 30 seconds and ping the C2 for a job. The C2 would respond, telling these apps to spoof a playback. But rather than actually show an ad, the TopTopSDK would merely call the reporting APIs specified in the chosen ad and indicate the video ad has been “shown.”
PARETO created realistic pingbacks, verifying that the phone was a “real” CTV streaming product in order to evade detection. They were dynamically configurable, so a single infected Android phone could rotate, selling traffic to many different buyers while assuming many different identities. PARETO’s operators periodically adjusted the balance of which streaming TV products were spoofed. They even wrote code specifically to attempt to bypass multiple fraud verification providers.
For the Roku-focused operation, the organization listed as developer for a collection of 36 apps on the Roku Channel Store which contact and receive instructions from the same C2 server, is named Playtium. The Roku app developer Playtium links to TopTop Media in their Privacy Policy:

Playtium Privacy Policy Linking to TopTop Media
Source: HUMAN’s Satori Threat Intelligence & Research Team
When these Playtium Roku apps—installed on real Roku devices—boot up, they contact a Playtium server for ad configurations. In the traffic analysis of this connection, HUMAN spotted the apps calling home to the same C2 server managing the PARETO botnet:
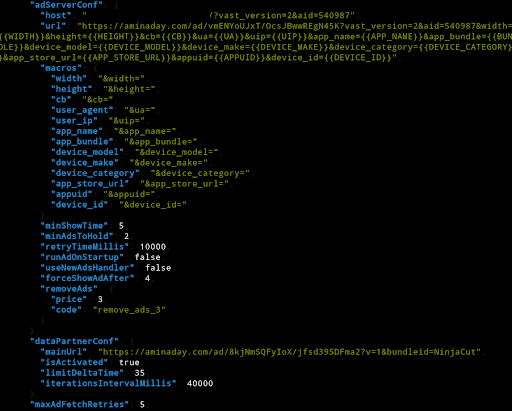
AdConfig Section of NinjaSlash Roku App
Source: HUMAN’s Satori Threat Intelligence & Research Team
Notice the aminaday[.]com address in the URL – that corresponds to the same C2 server observed in the Android-based PARETO apps. HUMAN also observed a VAST XML file served by that C2 server to these Roku apps running on real Roku devices, spoofing other streaming TV products:
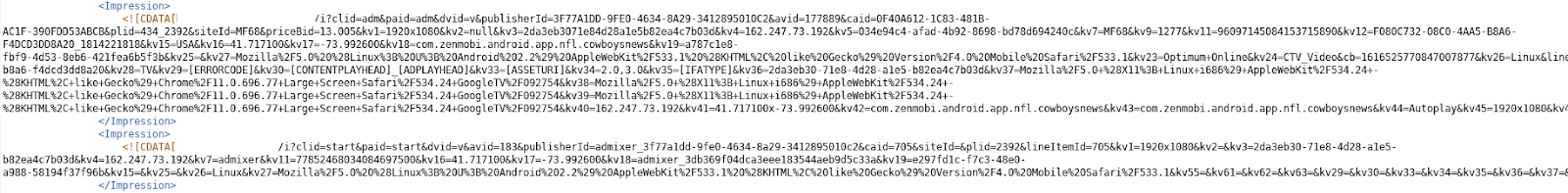
VAST XML Served by C2 Server, Spoofing Multiple CTV Devices
Source: HUMAN’s Satori Threat Intelligence & Research Team
HUMAN is actively working with the Roku team to continue our research.
How Did We Find Them?
Here’s a screenshot—which should look familiar—of the TopTopSDK within one of the PARETO-connected apps:

toptop.sdk is the name of the SDK in Android apps.
Source: HUMAN’s Satori Threat Intelligence & Research Team
On their own website, TopTopMedia shortens this name to “TTM”:
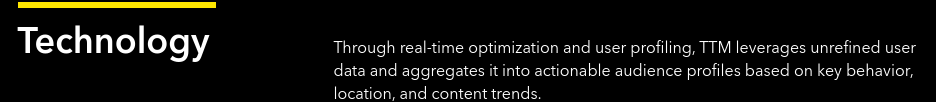
TopTopMedia referring to itself as TTM on its site.
Source: HUMAN’s Satori Threat Intelligence & Research Team
This name shortening is notable, as it correlates to a reference to the operation’s SDK as seen in the traffic associated with the botnet:
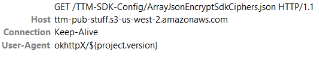
References to TTM in botnet traffic
Source: HUMAN’s Satori Threat Intelligence & Research Team
HUMAN continues to monitor the operators behind PARETO. As noted earlier, HUMAN has turned over information about the operations to law enforcement.
The Takedown and Aftermath
Many different parts of the internet were impacted by this operation: device manufacturers, advertisers, app stores, nearly a million people with Android phones, and an unknown number of downloads of certain Roku apps. With such a large web hanging over all of these entities, collective protection is imperative.
At HUMAN, when we see an operation affecting one customer, we can develop defenses to protect all of our customers. That’s why we created The Human Collective, and why their involvement in this takedown is an example of how collective protection works.
For PARETO, we developed algorithms to protect our customers and partners from PARETO attacks. Additionally, we are working with device manufacturers impacted by PARETO to develop new standards that will make it a lot harder to successfully run such operations in the future. As for the apps, we notified the Google Play Store and Roku Channel Store teams, and they have taken down all of the apps in both operations. And we’ve shared our findings with law enforcement.
It takes a collectively-protected ecosystem to prevent operations like PARETO. But the work isn’t finished. There’s still a lot of work to be done in the effort to protect the internet from bot attacks. And as shown in these operations, bots can be weaponized to take advantage of any platform – no matter your industry.
Within the CTV industry, we believe there are ways stakeholders can help in the fight against cybercrime:
CTV is still new and as the industry adopts standards, fraudsters will find the holes. Stopping bot attacks is a cybersecurity issue, not a measurement issue, and should be treated as such.
If you believe your business has been impacted by PARETO, please reach out to [email protected]. For a list of all of the Android and Roku apps associated with these operations, please read our technical analysis of PARETO.
