What is credential stuffing? | Definition, attack types, & solutions
Back to glossaryDefining credential stuffing
Credential stuffing is a type of cyberattack where bots are used to test lists of stolen usernames and passwords across different websites and web apps. If a login is successful, the validated credential pair is used to take over accounts and to execute fraudulent activities.
Credential stuffing attacks pave the way for account takeover (ATO), which occurs when criminals gain unauthorized access to user accounts. Once an account is taken over, criminals have free rein to commit all types of fraud. This includes making fraudulent purchases with stored credit cards, transferring gift card balances and loyalty points, posting fake reviews and submitting fake warranty claims and credit applications.
How it works
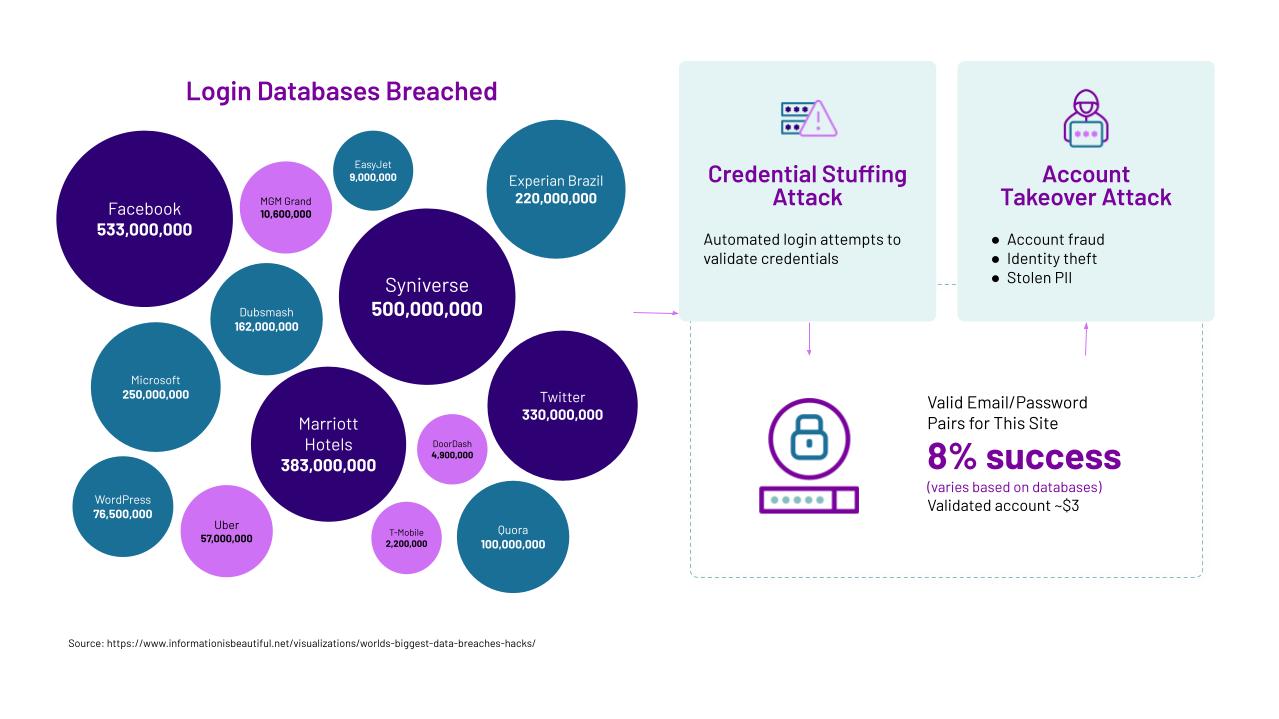
Modern credential stuffing attacks are cheap and easy to launch. Attackers obtain a list of stolen credentials, most commonly by buying a list off the dark web. A 2022 investigation found over 24 billion username and password pairs up for sale, and that number has only grown since then. Other methods of stealing credentials include PII harvesting, phishing and malware.
After procuring stolen credentials, cybercriminals deploy an army of bots to attempt thousands of logins on sites across the web. The login requests are typically spread out over multiple sites simultaneously to make the attacks harder to detect. E-commerce sites, financial institutions, online gaming and email accounts are popular targets.
A Harris Poll found that 66% of people use the same password for more than one online account. Users may not change their password after being notified of a data breach, or they may only reset it on one site but not another. This allows cybercriminals to use and re-use the same credentials in attacks on multiple sites.
If the credentials work and bots gain access to an account, they can proceed as the legitimate account owner. This results in an ATO, allowing the criminal to steal the value stored in an account. The stolen credentials can then be resold on the dark web, continuing the web attack lifecycle.
Impact of attacks
Simply put, credential stuffing attacks are bad for business. A recent report from the Office of the New York State Attorney General found that companies lose an average of $6 million annually due to credential stuffing attacks. Here’s how:
- Revenue loss: When cybercriminals make fraudulent purchases with stored cards, companies must supply refunds and restock lost merchandise. In addition, the rising number of chargebacks has led credit card companies to increase processing fees.
- Reputation damage: Brand reputation and consumer trust will suffer if users fall victim to identity theft or account fraud. In fact, nearly 60% of consumers won’t buy from a company that has experienced a cyberattack in the past year.
- Operational costs: Bot traffic slows website performance, increasing cost for bandwidth and frustrating users. This requires internal IT resources to manage bot traffic, as well as customer service resources to respond to complaints.
- Regulatory fines: Regulators are increasingly calling on businesses to be held accountable for cyberattacks against their sites. Dunkin’ Brands agreed to pay $650,000 in penalties and costs following a credential stuffing attack.
A 2022 report from the Office of the New York State Attorney General, reported as many as 193 billion credential stuffing attacks in the span of one year. It can be argued that these numbers will only rise as online activity continues to increase year over year, causing more headaches for businesses and consumers. For consumers, it means being locked out of personal accounts, loss of personal data, unauthorized purchases, and stolen gift card and loyalty point balances. For businesses, it means warranty fraud, lost customers, high operational costs, and an IT burden to manage bad bots.
Detection & prevention
Detection
Awareness is the key to detecting credential stuffing attacks. The following warning signs might mean credential stuffing bots are targeting a site:
- Multiple login attempts on multiple accounts within a limited timeframe
- A higher-than-usual login failure rate
- An increase in password reset requests by users whose accounts were part of the attack
- Website downtime caused by an increase in site traffic
The absence of these warning signs doesn’t mean bots aren’t lurking. Bots are often deployed to multiple sites simultaneously, so they don’t call attention to themselves. This means that login rates on a particular site may not be alarmingly high and there’s no lag in site speed that would normally sound an alarm.
As bots become increasingly sophisticated and programmed to evade defenses, they can more easily fly under the radar. If companies want to keep pace, they must focus on behavioral anomalies and characteristics to stop credential stuffing attacks. This means paying attention to user interactions, mouse movements and clicks, keyboard patterns and the rate of response between pages, and then benchmarking them against a baseline.
Prevention
Preventing credential stuffing attacks requires a layered approach. The following techniques can help:
- Verification challenges: Traditional verification challenges include CAPTCHA and reCAPTCHA, though sophisticated bots and farms can often solve those tests. Developers have responded by making CAPTCHAs harder, but this only annoys human consumers and leads to abandonment. The Human Challenge blocks bots without frustrating human users.
- Rate limiting: Websites can limit the amount of login requests in a given time, slowing fast-moving credential stuffing bots and encouraging them to move on to another site. Web application firewalls (WAFs) can rate-limit traffic, but they cannot detect bots that mirror human behavior or botnets that rotate through thousands of different IP addresses.
- Proof of work: Proof of work (PoW) requires a user’s device to expend computational effort before the user can log in. If an attacker is executing many logins simultaneously, PoW will consume a lot of energy and CPU cycles. This makes it expensive for cybercriminals to execute credential stuffing attacks and disincentivize them from launching future attacks against your site.
- Monitor compromised credentials: Website owners can leverage databases of stolen usernames and passwords that are actively being used in credential stuffing attacks. This early warning system stops attackers from logging in with compromised credentials and flags them for mitigating action — such as an out-of-band password reset — preventing fraud before it is committed.
Stop attacks with HUMAN
HUMAN Account Takeover Defense combats credential stuffing attacks using a two-pronged approach:
- Blocks logins with stolen credentials being used in real-world attacks, reducing your vulnerable attack surface
- Stops bot attacks at login, blocking automated login attempts in real time
Account Takeover Defense offers Human Challenge, the first user-friendly verification tool that protects web and mobile applications by presenting a visual challenge to help easily differentiate humans from bots. Solve times for Human Challenge are four to six times faster than reCAPTCHA, and abandonment rates are three to five times lower — a winning combination.
Account Takeover Defense stops credential stuffing attacks with unparalleled accuracy. The solution safeguards online revenue, protects brand reputation and improves operational efficiency, all while preserving user experience.