Web Application Firewalls (WAFs) are essential for protecting web applications by filtering and monitoring HTTP/HTTPS traffic, and mitigating threats such as SQL injection and cross-site scripting (XSS). While WAFs and the more comprehensive WAAPs (Web Application and API Protection) are vital components of cybersecurity, they are not sufficient to address sophisticated bot threats and human-led fraud.
What is a Web Application Firewall (WAF)?
A web application firewall (WAF) is a security tool that filters and monitors HTTP/HTTPS traffic between a web application and the internet. It operates at the application layer and is specifically focused on detecting and blocking malicious traffic targeting web applications. WAFs use a variety of techniques to identify and mitigate threats, such as SQL injection, cross-site scripting (XSS), file inclusion, and other application-layer attacks.
WAFs focus on protecting web applications from application-layer attacks that exploit vulnerabilities in the application code. They act as a reverse proxy, sitting between web clients (browsers, etc.) and the web application server. There, they analyze HTTP/HTTPS traffic (i.e., requests and responses) and block malicious requests that match known attack patterns or violate defined security rules.
WAFs vs. Bot Management: Identifying the Security Gap
WAFs filter and block malicious traffic based on a set of rules or policies. Though WAFs often have basic bot mitigation capabilities, such as blocking based on IP addresses or user-agent strings, these static rules are not designed to handle sophisticated bots that mimic human behavior and continually adapt to evade detection.
CDN providers themselves acknowledge that bot management is a necessary supplement to the traditional WAF. In fact, many WAF vendors offer machine learning-based bot management solutions to specifically manage automated traffic. However, even add-on solutions from your WAF vendor are often not enough to combat the most advanced bot attacks, such as account takeover, scraping, fake account fraud, and transaction abuse. And WAF add-ons do not address downstream human-led account abuse and fraud.
Beyond Basic Protection: Where WAF Add-Ons Fall Short
Specialist cyberfraud solutions offer advanced detection, mitigation, and reporting capabilities to protect against sophisticated bots and human-led fraud, which CDN and WAF add-on tools often lack. Depending on your business needs, it might be necessary to opt for a specialist standalone solution or to add it as an extra layer of defense to the tool provided by your CDN/WAF vendor. Here are five areas to consider when making that choice:
Specialist Cyberfraud Solutions vs. WAF Add-Ons: A 5-Point Comparison
Sophistication of Detection Models: Advanced Threat Analysis
Add-on solutions can sometimes be sufficient to mitigate common, one-and-done attacks. However, if your application is targeted by sophisticated adversaries, you will need a specialist solution with a more advanced detection engine.
Customization and Extensibility
Single-method security solutions are incomplete. Modern security requires sophisticated threat detection and mitigation that works regardless of the cybercriminal tactic. This demands adaptive decisioning and customizable response actions to neutralize both automated and human-led attacks tailored to your environment and business.
Full Lifecycle Mitigation: Pre- and Post-Login
Fraudsters are increasingly using a mix of bot attacks and illicit human behavior to commit fraud. Security teams must mitigate threats across the entire account lifecycle during every user session. This means stopping activity with malicious intent, regardless of whether it is carried out by humans, automation, or AI.
Visibility and Reporting
Everyday consumers and cybercriminals alike are increasingly using a mix of bots, AI agents, and manual engagement to search, shop, stream, and socialize online. It is critical to understand the authenticity and intent of every interaction, regardless of whether it is carried out by a bot or human.
Support and Management
Though add-on solutions may be easier to spin up with fewer resources, they require your team to manage the ongoing maintenance of rules and policies across web and mobile — or you may have to outsource it to a costly managed services team.
Choosing the right approach
In some cases, organizations might choose to deploy both an add-on and a specialist solution in tandem. It all comes down to your unique needs, which is why selecting a solution with business outcomes in mind is critical.
HUMAN uses adaptive machine learning and AI models to provide outcome-centric, customizable detection and mitigation that spans the entire lifecycle of bot attacks and fraud—as well as robust investigative capabilities that enable deep understanding of your unique threats. The solution helps protect organizations from account takeover, scraping, new account fraud, transaction abuse, and other attacks throughout the customer journey—from the very first interaction with a website or app, through to the day-to-day usage of accounts.
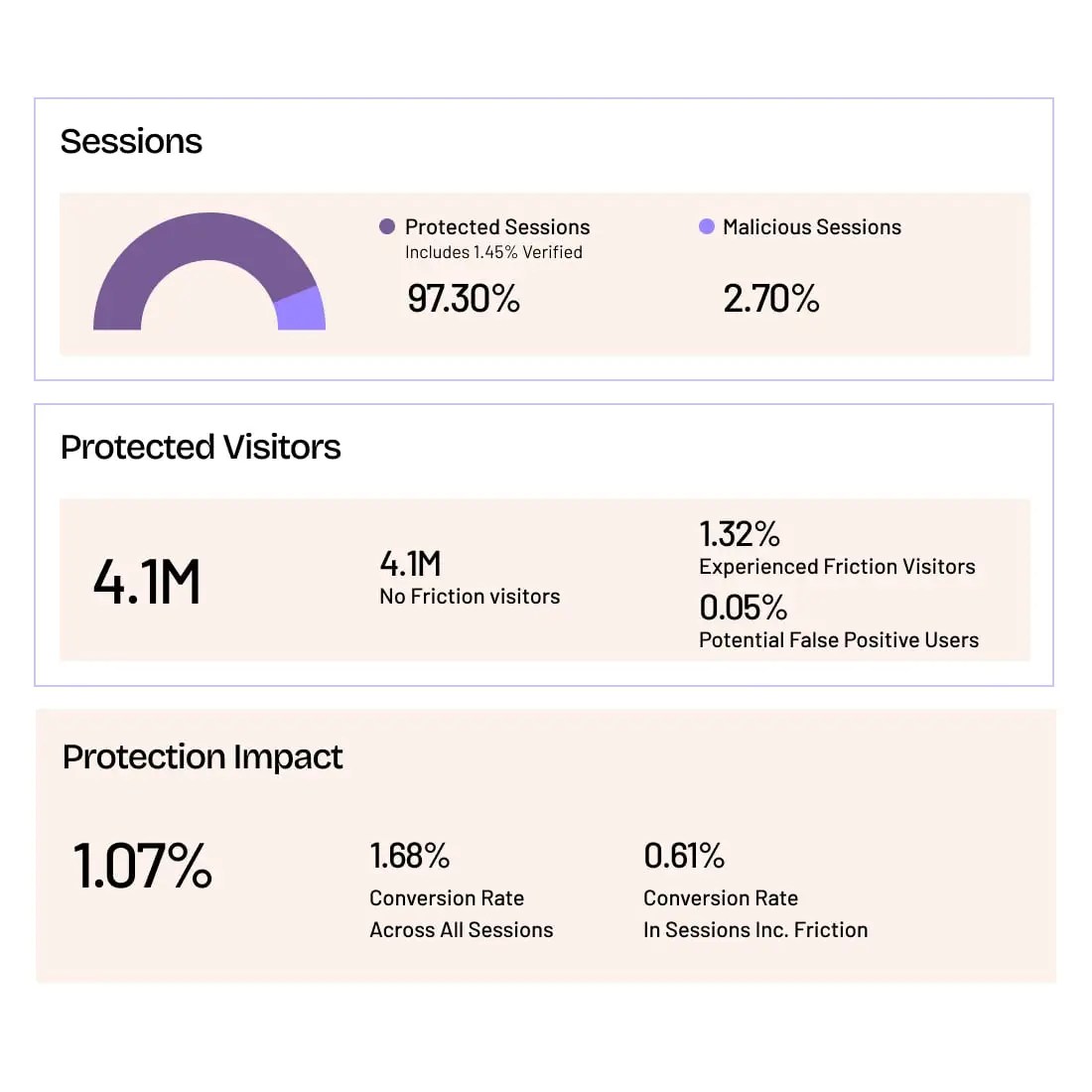
Grow with Confidence
HUMAN Sightline protects every touchpoint in your customer journey. Stop bots and abuse while keeping real users flowing through without added friction.