Researchers: Louisa Abel, Lindsay Kaye, João Marques, Vikas Parthasarathy, João Santos, Adam Sell
IVT Taxonomy: Misleading User Interface
HUMAN’s Satori Threat Intelligence and Research Team has uncovered and disrupted a sophisticated ad fraud and click fraud operation dubbed SlopAds. The threat actors behind SlopAds operate a collection of 224 apps and growing, collectively downloaded from Google Play more than 38 million times across 228 countries and territories. These apps deliver their fraud payload using steganography and create hidden WebViews to navigate to threat actor-owned cashout sites, generating fraudulent ad impressions and clicks. The threat actors’ infrastructure and many of the apps share an AI theme, contributing to the name of the operation.
The apps are managed by several command-and-control (C2) servers and dedicated promotional domains; the extensiveness of this network of C2 servers and traffic-driving domains suggests the threat actors have plans for expanding the SlopAds operation. During the assembly of this report, the threat actors behind SlopAds continued to adapt and attempt to stage new apps to Google’s Play Store.
SlopAds stands out for its novel use of attribution and measurement tools as an obfuscation tactic. Only downloads that could be traced to a threat actor-run ad campaign attempted downstream ad and click fraud attacks; downloads that were unconnected to the ad campaign did not attempt fraud.
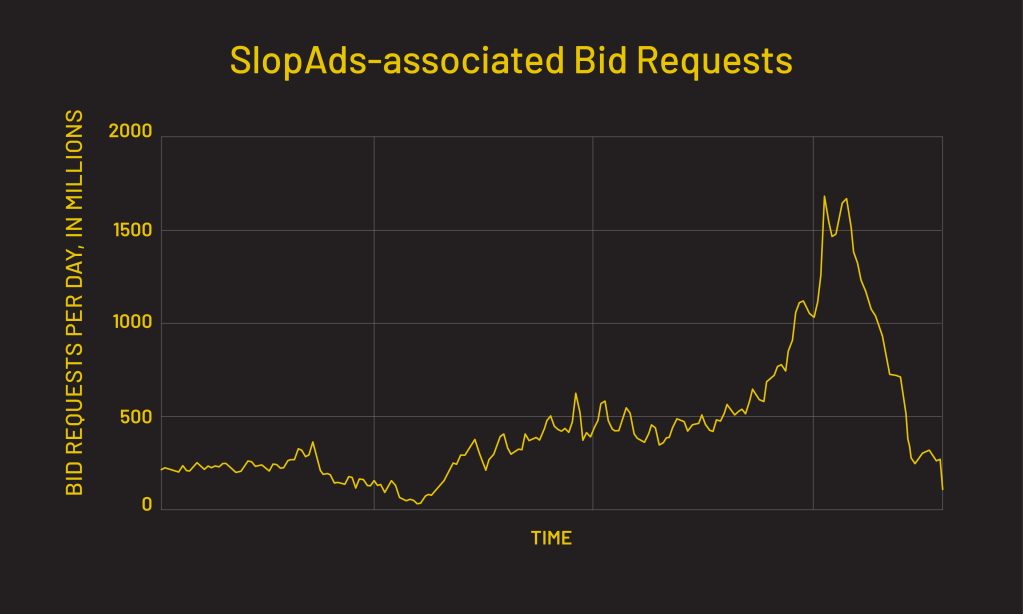
At its peak, SlopAds accounted for 2.3 billion bid requests a day. Traffic from apps associated with SlopAds came from all over the world, but was heaviest in the United States (30%), India (10%), and Brazil (7%).

Researchers dubbed this operation “SlopAds” because the apps associated with the threat have the veneer of being mass produced, a la “AI slop”, and as a reference to a collection of AI-themed applications and services hosted on the threat actors’ C2 server:

Please note: services shown in the screenshot above are not the official services; they’re hosted tools operated by the threat actor.
Researchers also observed the threat actors training an AI tool hosted on the same domain:
Customers partnering with HUMAN for Ad Fraud Defense and Ad Click Defense are protected from the impact of SlopAds and can reach out to their HUMAN account team for more information.
Google removed all of the identified apps listed in this report from Google Play. Users are automatically protected by Google Play Protect, which warns users and blocks apps known to exhibit SlopAds associated behavior at install time on certified Android devices, even when apps come from sources outside of Play. All users who have these identified apps installed on their device will receive a warning and will be prompted to uninstall them. Play Protect is on by default on Android devices with Google Play Services.
How SlopAds Works: A Multi-Layered Ad Fraud Scheme
The threat actors behind the SlopAds operation took great pains to cover their tracks and make it difficult for the cybersecurity community to unpack and understand how the scheme worked. From developing and publishing apps that only commit fraud under certain circumstances to adding layer upon layer of obfuscation, SlopAds reinforces the notion that threats to the digital advertising ecosystem are only growing in sophistication.
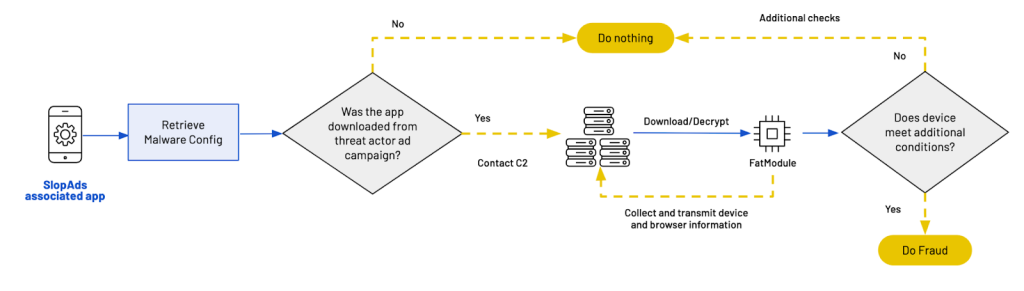
Delivery and Obfuscation Tactics
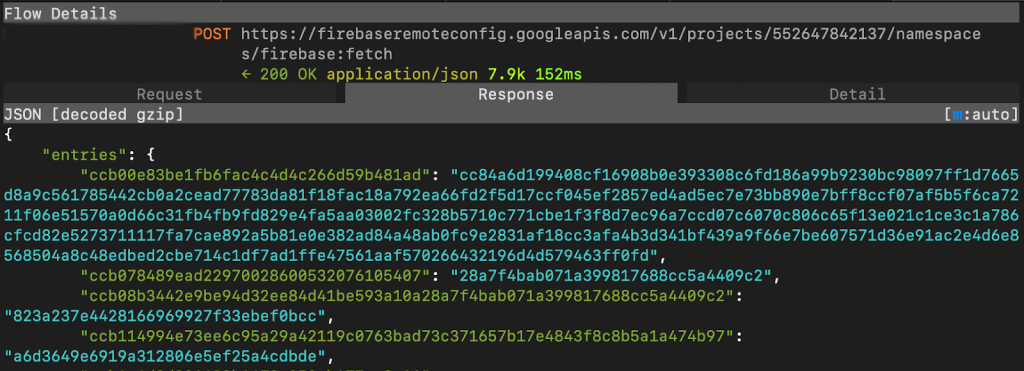
When a SlopAds-associated app is downloaded, the app uses Firebase Remote Config, a Google tool, to retrieve an encrypted configuration with a set of URLs: one for downloading the ad fraud module (FatModule), URLs for a collection of H5 cashout domains, and one with a JavaScript payload powering the click fraud attack.

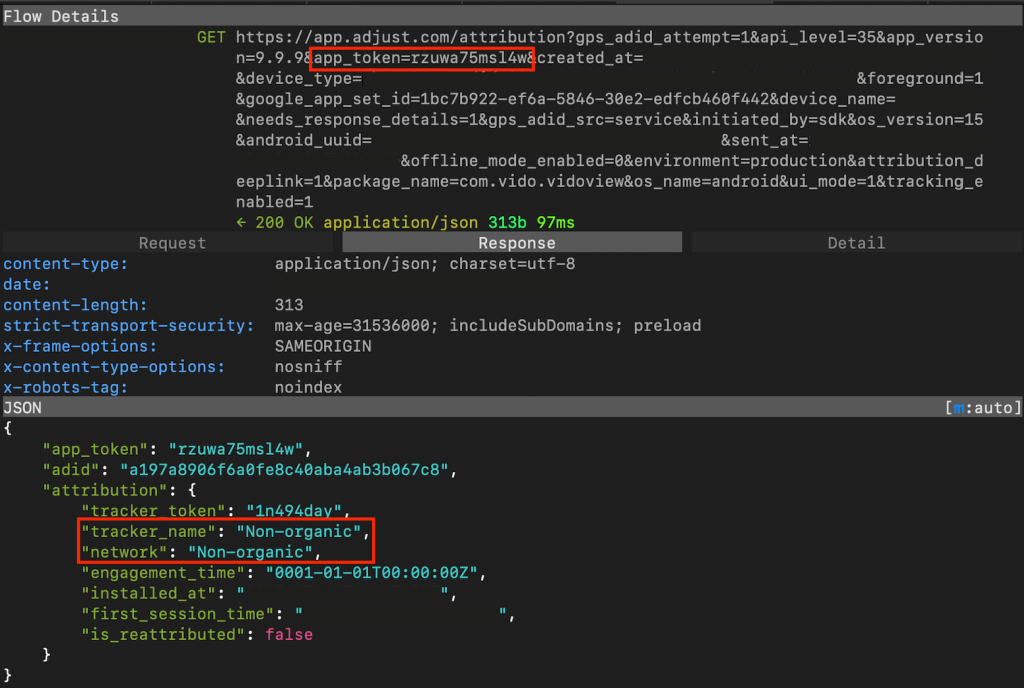
Then, the app performs the first of several checks, the results of which determine whether the app will proceed to attempt ad fraud or not. This first check is to determine whether the app was installed organically (i.e., by a user visiting the Play Store directly and downloading the app) or non-organically (i.e., the user clicked on an ad and was taken to the Play Store listing for the app). SlopAds uses a mobile marketing attribution platform to accomplish this, checking whether a tag associated with that platform is present within the web request. This abuse of marketing attribution technology is a novel approach to ad fraud, and underscores the growing sophistication of threat actors’ tactics.
If the app was organically installed, it will behave as described in the Play Store description and not attempt any fraud. If the app was downloaded following an ad click, however, the app will contact its C2 server to download the ad fraud module, FatModule.
If the app passes this first check, the C2 will deliver four PNG files that, through digital steganography, hide an APK that, decrypted and reassembled, form FatModule, the module that manages the fraud:
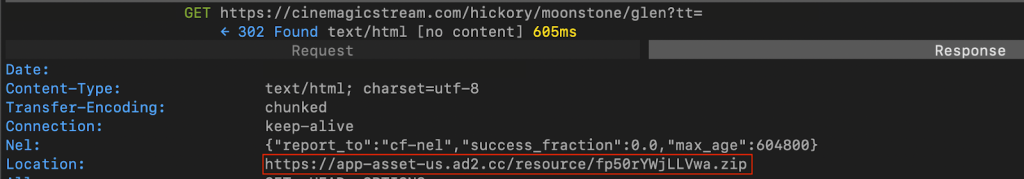

These PNG files were only partially the images you see above – the rest of the delivered files were pieces of FatModule, which are reassembled on the user’s device to form the code that carries out the fraud.
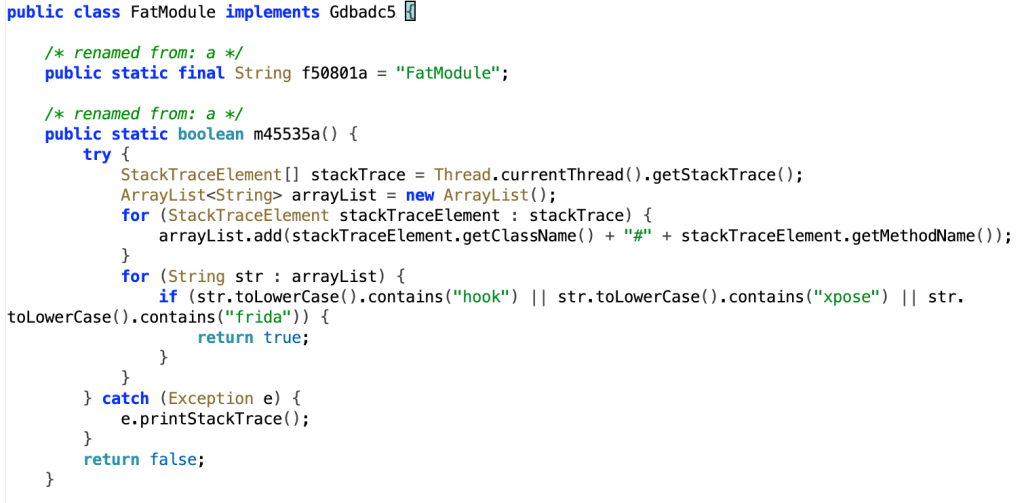
Apps associated with SlopAds perform a debugging check, searching for any indications the app is being picked apart using debugging tools which might expose the fraud:
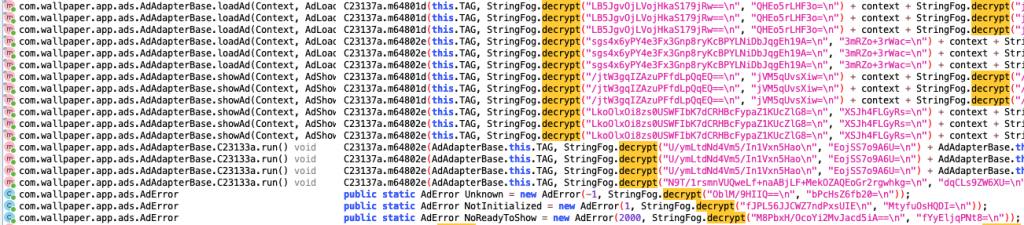
Additionally, strings within the SlopAds-associated apps are encrypted:
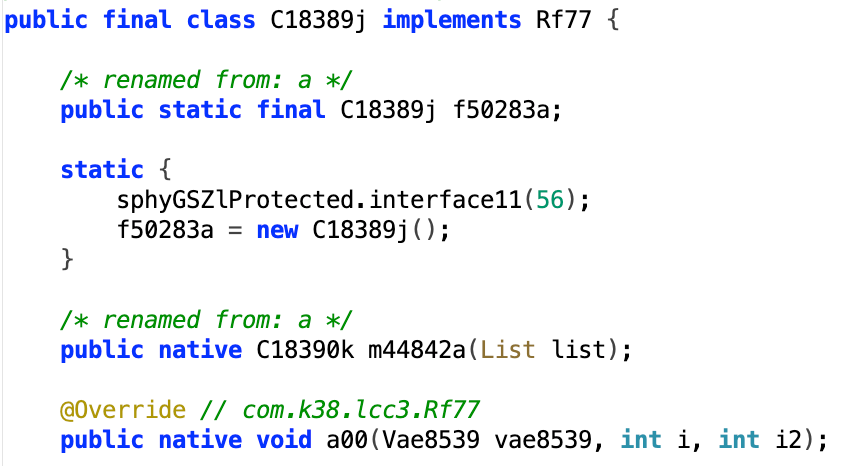
Apps associated with the threat include packed native code, a technique that hides the code’s true intent on first glance.
Information Collection and Fraud
The fraud schemes connected to SlopAds all take place within hidden WebViews, which are similar to web browsers but with fewer features.
Gathering Device Information
Following the install and debugging checks, SlopAds-associated apps launch a hidden WebView and navigate to a website that captures device and browser information.
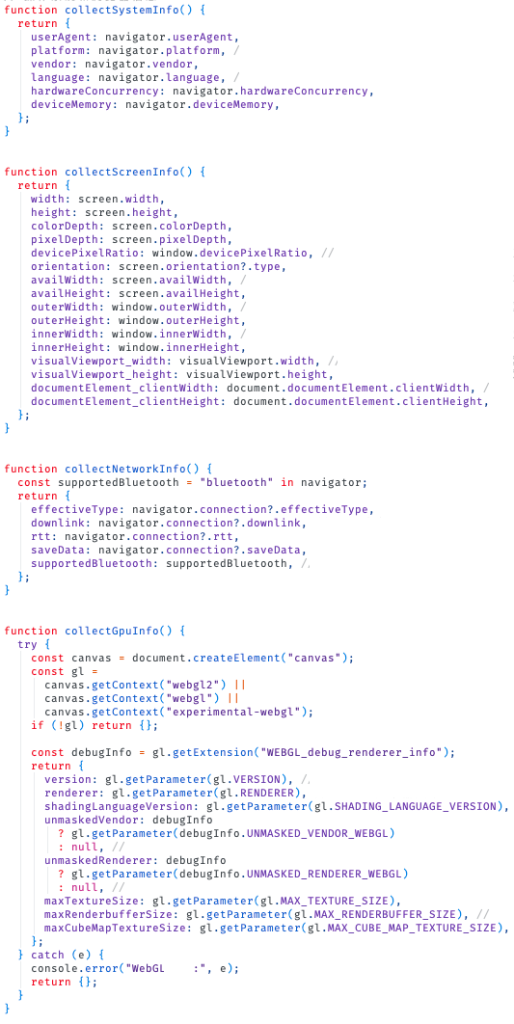
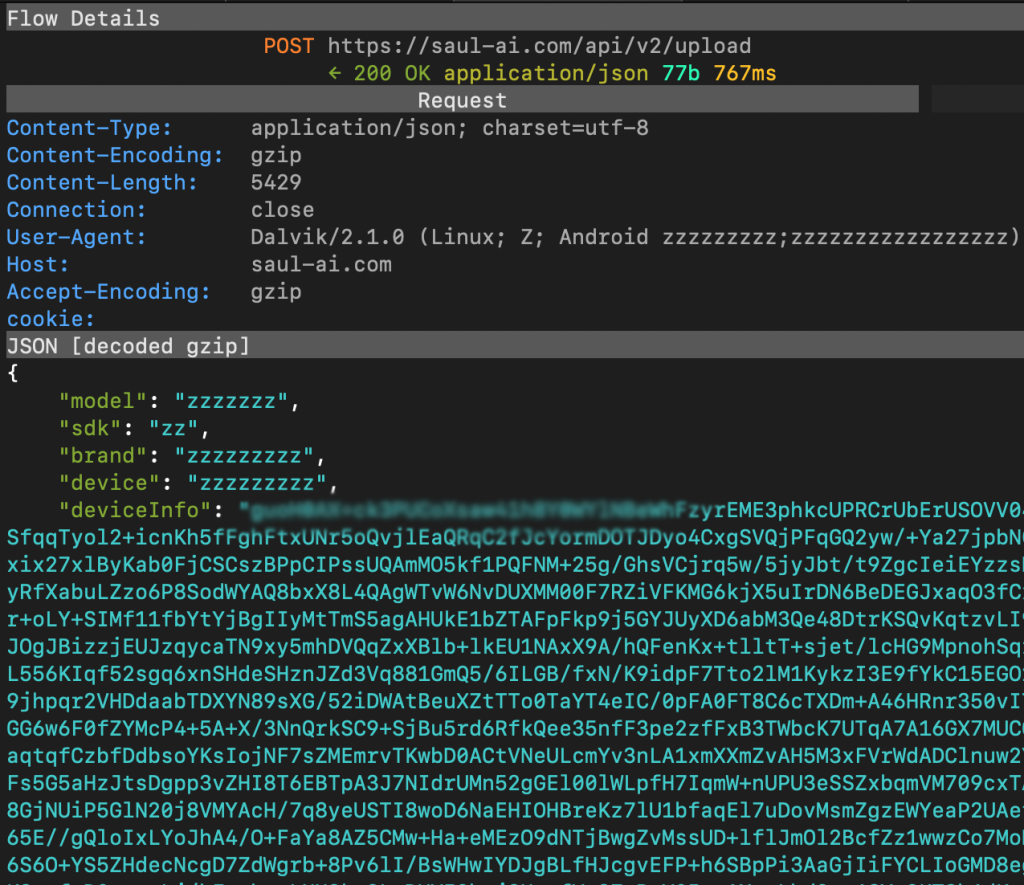
Bottom: POST request capturing the data
This step also includes one final pre-fraud check, this one for the presence of an emulator or signs the device is rooted:
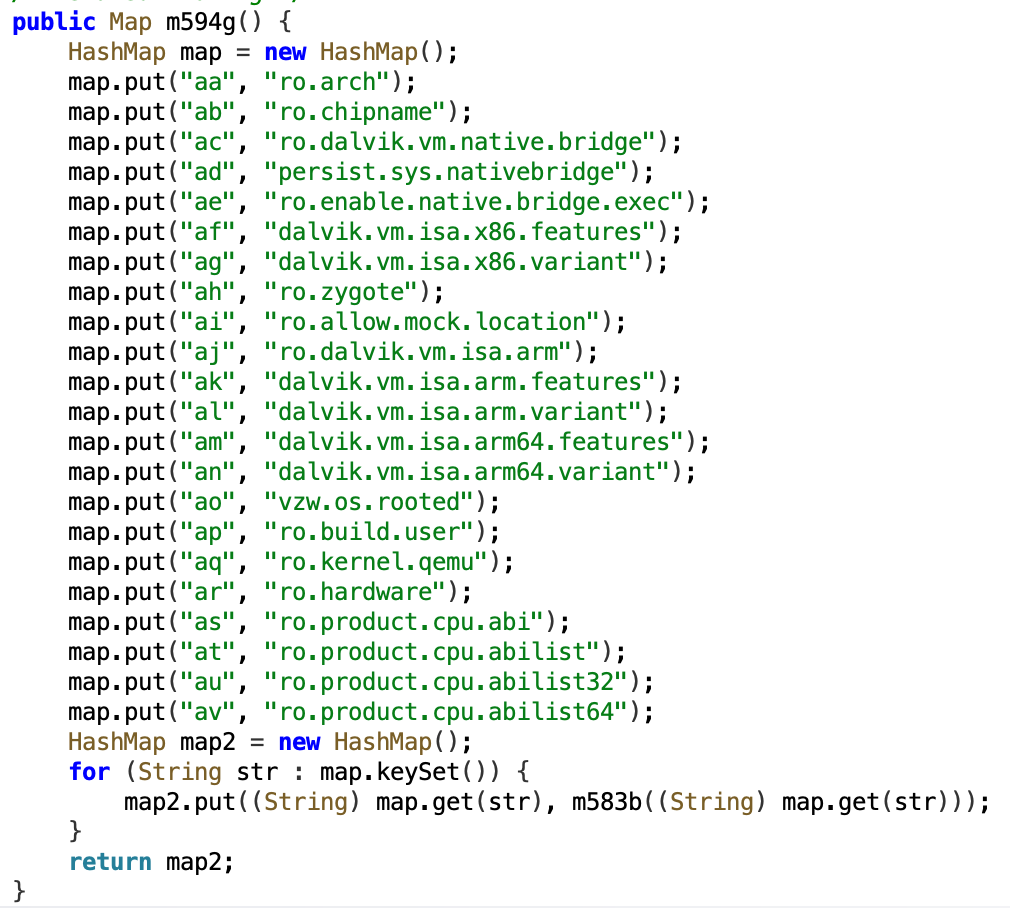
This information allows the threat actors to target specific devices, as the code prevents the scheme from continuing if certain conditions aren’t met. While not observed directly in this operation, researchers have seen similar information captures used to create legitimate parameters—like user-agent/browser combinations—enabling threat actors to carry out separate or subsequent attacks, like SSAI spoofing attacks.
Ad and Click Fraud
After the first hidden WebView collects device and browser information, apps associated with SlopAds retrieve information from the C2 server on what domains to visit in further hidden WebViews. These domains host cashout sites owned by the threat actors.
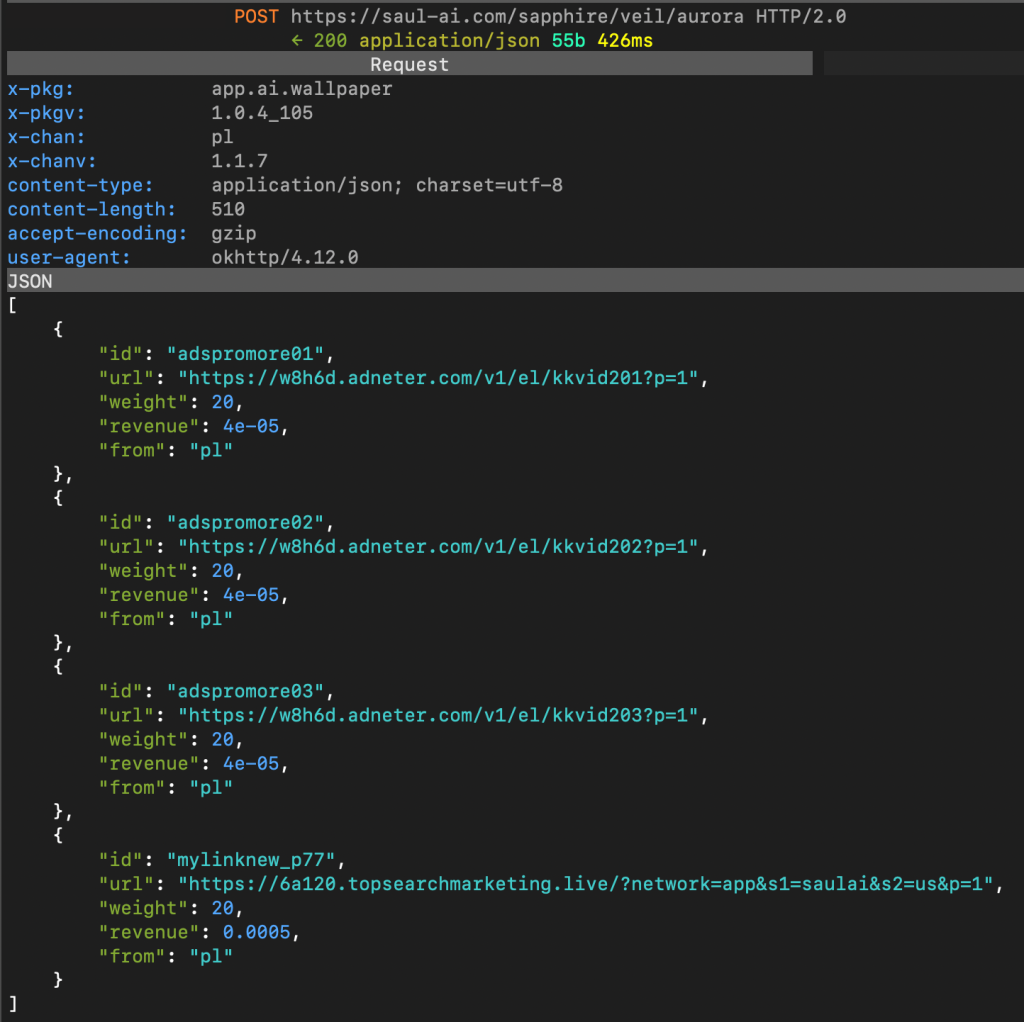
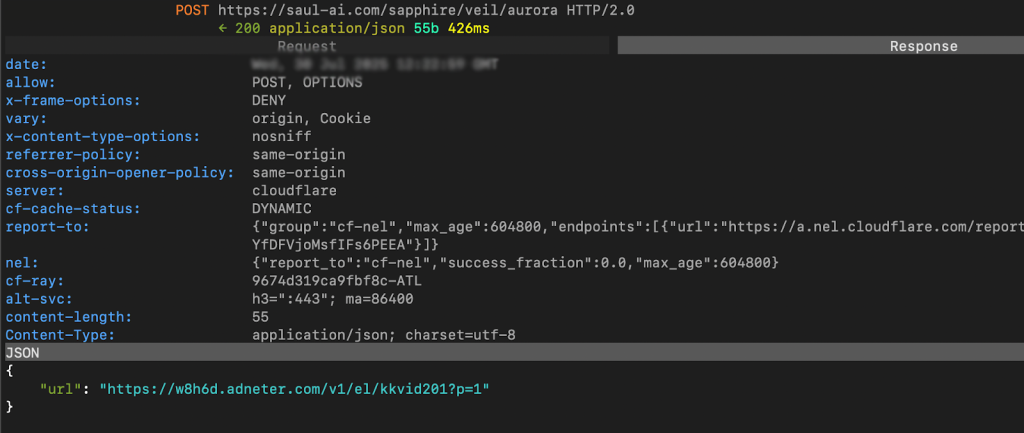
Notice the URL field in the screenshots above: all of them have parameters after the top-level domain. Satori researchers believe these parameters inform the domains that the traffic is related to the SlopAds operation and should request and render ads.
The domains redirect several times, changing tracking parameters multiple times. This sanitizes the referrer data connected to the ad requests, making the requests look more legitimate.
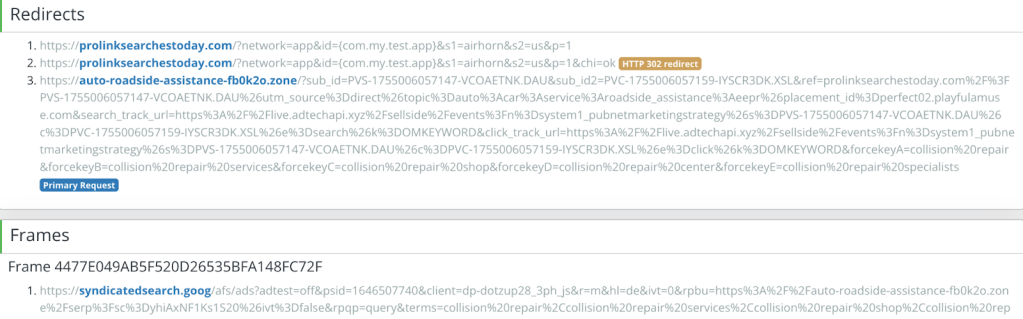
One cashout mechanism for SlopAds is through HTML5 (H5) game and news websites owned by the threat actors. This cashout mechanism is similar to what researchers found in the recent BADBOX 2.0 scheme. These game sites show ads frequently, and since the WebView in which the sites are loaded is hidden, the sites can monetize numerous ad impressions and clicks before the WebView closes.
SlopAds also includes code that instructs the hidden WebView to only click on viewable ads on the cashout websites.
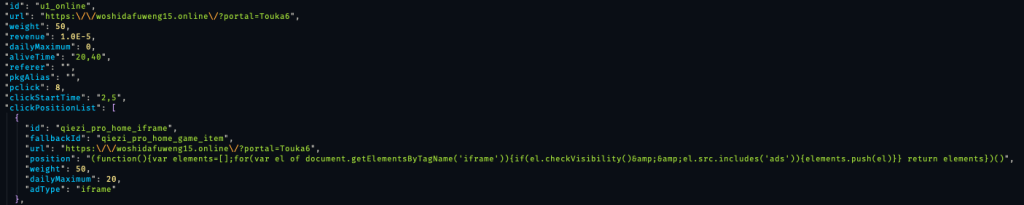
Finding and Disrupting SlopAds
Satori researchers uncovered SlopAds while investigating anomalous patterns in the data within HUMAN’s Ad Fraud Defense solution. These anomalies led researchers to examine a collection of domains promoting SlopAds-associated apps.
These promotional domains, which have little function other than pointing users to the Play Store, share a common infrastructure, link back to a domain—ad2[.]cc—which is the threat actors’ tier two C2.
Researchers examined similarities in the C2 domain and found more than 300 related domains promoting SlopAds-associated apps, suggesting that the collection of 224 SlopAds-associated apps may be only the beginning for this threat actor. Researchers observed the threat actor testing and ramping up traffic quickly:
Researchers have been in contact with the Google Play Store team about SlopAds, and apps associated with the threat are removed from the Play Store as they’re uploaded and identified.
Conclusion: HUMAN Protects Customers from Sophisticated Threats
Customers partnering with HUMAN for Ad Fraud Defense are protected from the impact of SlopAds. The sophistication of SlopAds suggests the threat actors will likely adapt their scheme again to try to continue to defraud the digital advertising ecosystem. Satori researchers continue to monitor the threat actors for new adaptations and new apps associated with SlopAds.
IOCs

Your Industry Guide to Click Fraud in 2025
Understand evolving fraud tactics, see where vulnerabilities exist, and learn how to protect ad spend across the ecosystem.

