In the world of online gambling, fraud has evolved from simple manual schemes to highly automated, sophisticated attacks targeting critical systems after users log in. One of the most dangerous emerging threats is the deposit attacks, in which fraudsters exploit vulnerabilities in the deposit and withdrawal process, draining account funds and crippling platforms. In this post, we’ll explore how these attacks unfold, how they span the entire user journey (from account takeover attempts to post-login abuse), and how organizations can fight back with a full-lifecycle protection approach.
When Attacks Hit After Login: Defending the Full User Journey
The online gambling industry faces a sophisticated and evolving threat landscape that spans the entire user journey. Before the login stage, bots can register fake accounts to harvest sign-up bonuses or scrape information to support their bets. At login, large-scale credential stuffing runs stolen username-password pairs, producing confirmed logins for account takeover. But the most damaging activity occurs post-login when attackers—armed with either hijacked legitimate or synthetic profiles—operate from authenticated sessions that appear completely normal.
Inside those sessions, fraudsters run schemes that manipulate odds, drain balances, launder funds, or even mount denial-of-service–style queue jams. Because the traffic comes from valid accounts that behave in ways that mimic genuine user behavior, these post-login fraud operations routinely evade controls that focus only on overt login anomalies. Stopping these attacks demands full-lifecycle protection that links the bots creating or compromising accounts with the fraud they carry out after login, ensuring no stage of the journey is examined in isolation.
What are Deposit Attacks?
One particularly dangerous post-login threat observed by HUMAN’s Account Defense and Satori Threat Intelligence teams is the deposit attack. These are typically automated (or manual-automated hybrid) attacks aimed at disrupting or even exploiting the deposit or withdrawal process on a platform. They often involve carding, fund draining, or other financial crime schemes and are executed at scale using cracked accounts or fake ones created for abuse.
While deposit attacks have been especially visible in online gambling fraud, any platform that allows users to add/withdraw funds or that uses queued processes (ticketing services, online games, food delivery, fintech apps, etc.) could be at risk. These attacks often leverage the fact that they occur from authenticated accounts, making the malicious activity blend in with normal user behavior. Traditional fraud detection tools that focus on login or transaction anomalies in isolation often fall short against deposit attacks–the activity looks legitimate on the surface and doesn’t trigger simple rule-based alerts.
Let’s take a more detailed look at two types of Deposit Attacks observed by HUMAN in the online gambling industry: Line Jamming and Topping and Draining. Identifying these tactics enabled HUMAN to enhance our detection and mitigation efforts—underscoring how quickly the threat landscape continues to evolve.
Jam the Line: Denial-of-Service via Fake Deposits
In one case, we successfully protected a gambling platform against a Denial-of-Service-style Deposit Attack, believed to have been orchestrated by its competitors.
As part of regulatory requirements, this platform’s deposit process mandates that users complete a short verification, including an SMS-based OTP and submission of personal details, before funding their account. This verification window is time-limited and managed by an automated queue since only a fixed number of users are allowed to deposit simultaneously.
The attackers exploited this system by creating large networks of fake accounts that continually initiated the deposit verification process without ever completing it. By occupying an estimated 60–70% of the available deposit queue, these fake accounts effectively jammed the queue, preventing legitimate users from depositing funds. The impact was severe: while the queue was blocked, the platform saw significant revenue losses and a deteriorated user experience as frustrated users were unable to fund their accounts.
Detecting and Mitigating the Attack
HUMAN detected this attack by identifying the telltale behavioral pattern: accounts that repeatedly start a deposit but never finish it. By linking this pattern across dozens of accounts, the system isolated the malicious cluster of bots in real-time. Importantly, detection was achieved without relying on any sensitive user data (we never needed to examine personal details, card numbers, deposit amounts, etc.). Instead, the defense was powered purely by behavioral signals, account metadata, and technical fingerprints that distinguished fake accounts from real customers. Once the fraudulent accounts were identified, HUMAN swiftly mitigated the attack: the offending accounts were blocked and any new accounts spawned by the same bot infrastructure were automatically shut down. This behavioral approach allowed the platform to stop the attack in its tracks, protecting both its users and revenue while preserving legitimate users’ privacy and experience. Notably, all of this happened behind the scenes, and genuine customers simply saw the deposit system continue to function normally once the attack was neutralized.
Topping and Draining: Draining Funds from Compromised Accounts
In another case, attackers exploited a different safeguard put in place by a gambling platform – this time targeting protections designed to prevent fund draining. The platform had a rule that withdrawals could only be sent to credit cards that had previously made a deposit into the account. In theory, this ties withdrawals to a verified funding source. In practice, the attackers found a clever way around it, combining manual and automated methods in what we call a Topping and Draining attack.
Unlike the “Jam the Line” incident, which relied mainly on fake bot accounts, this attack involved real user accounts that had been compromised. The fraudsters acquired login credentials (likely via cracking or dark web purchases of leaked credentials) for a number of dormant user accounts that already had a positive balance. Once they logged in – essentially performing an account takeover on these accounts – they employed two approaches to drain funds:
Below is an example of a Topping and Draining session illustrating such an attack:
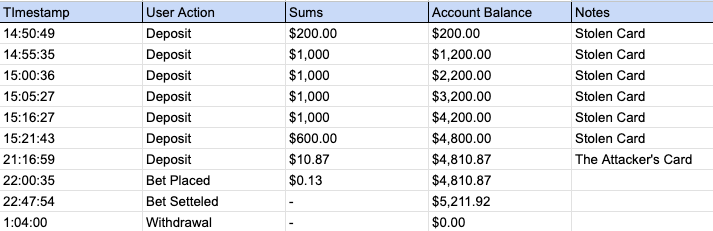
Once again, HUMAN’s Compromised Account Defense capabilities were instrumental in catching the scheme. The system continuously monitors user activity on both deposit and withdrawal endpoints, using machine learning algorithms to flag irregular sequences and behaviors. In this case, it detected anomalies that tied together a network of compromised accounts exhibiting similar patterns (e.g. multiple deposits from varied payment sources followed by rapid withdrawals). By analyzing behavioral flows, device and network signals, and enriched account metadata, the platform’s defenses not only neutralized the ongoing attack but also exposed related operations in the fraud campaign. In fact, the intelligence gathered during this incident helped identify early-stage attack infrastructure before those actors could launch further attacks on other accounts.
High Reward for Attackers, High Risk for Platforms
As bot kits and automation frameworks become more accessible, attacks that were once the domain of highly skilled fraudsters are now within reach of far less technical actors. This shift is especially evident in lucrative illegal activities like carding, account takeover fraud, balance draining, and money laundering. While some attacks are still carried out manually, the growing wave of cheap automation makes defending against them increasingly complex. In short, fraud operations are growing in scale, sophistication, and automation.
Today, online platforms across industries – gambling, retail, ticketing, travel, banking, and more – face a surge in coordinated fraud campaigns and hybrid bot/human attacks. These threats span the entire user journey, occurring before, during, and after login, and they target both end-users and the very systems put in place to protect those users. Ironically, as attacks become more human-like in behavior, businesses are often forced to introduce extra verification steps and security hurdles, which can frustrate customers and hurt the user experience. In cases like deposit attacks, we’ve even seen attackers weaponize the platform’s own security mechanisms (e.g. the deposit verification queue) against it – turning safeguards into chokepoints to exploit.
Defending against this new breed of fraud requires a holistic strategy. It’s no longer enough to just block bots at the front door or review transactions after the fact – the connections between events (a fake account creation, a login with stolen credentials, a series of odd deposits) must be understood in context. This is where HUMAN’s full-lifecycle protection makes a critical difference.
HUMAN’s unified approach empowers organizations to secure users, safeguard revenue, and preserve a seamless user experience – even as threats multiply. Our mission is to neutralize fraud, abuse, and automated attacks whether they’re carried out by bots, human fraudsters, or increasingly by AI-driven agents. By combining industry-leading bot mitigation with advanced fraud detection in one platform, we enable businesses to protect every digital interaction without compromising on usability.
To learn more about how HUMAN’s innovative solutions can help protect your organization from account takeover and automated fraud at every step of the user journey, we invite you to schedule a demo with our team. See first-hand how a unified, full-lifecycle fraud defense can safeguard your platform from threats before login all the way through post-login account abuse.
