Introduction:
The modern era of website frameworks and website development in particular is far more advanced, capable and customizable than ever before.
The current process of developing and maintaining a new website, such as a new e-commerce platform, has never been so easy to handle with so many options for different advertising, marketing, payment and analytics third party vendors and libraries which make life so much easier; they can both increase revenues significantly and minimize the hassle of handling and monitoring your own website. By simply adding a script tag to your own website’s framework, you can fully utilise dozens of different third party services right away.
However, this new opportunity does not come without a major security risk.
An average site hosts between 20-30 or more third party vendors and JavaScript libraries, which results in having several dozens to hundreds of different unique third party scripts running on your website. One of these scripts can potentially hold a security breach or vulnerability which can be exploited at any given time.
As Ben has mentioned in his blog post – “Changes to JavaScript libraries made in client-side attacks can alter website behaviour without site visitors noticing … These damages include manipulating the user experience, hijacking the user’s session, and leaking or stealing sensitive user data such as sensitive personal information, account passwords, and financial data like bank account or credit card account information.”
Background – Third Party Script Behaviour Change Analysis:
Using the HUMAN Code Defender sensor which is embedded across many top brands’ websites – we have a rare opportunity to peek into extremely interesting metrics of behavior patterns and changes of third party scripts throughout our customers’ websites.
Third party libraries and scripts are making ongoing changes and behaviour additions over time
Most websites seem to create requests to between 3-4 new network destinations on average on a weekly basis – these are requests that are being sent to new third party target URIs which can potentially contain sensitive PII or even payment information.
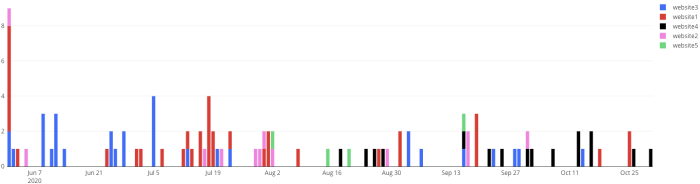
Looking on 5 of our top-tiered customers websites’ (5 million monthly page views and above) network deviations / newly contacted domains, this phenomenon gets even more pronounced:
No. of new domains contacted over time:
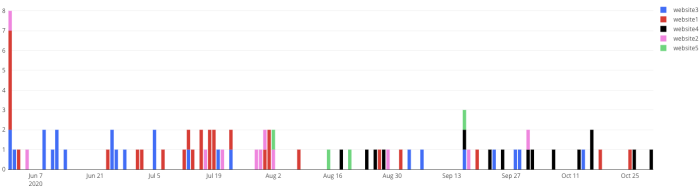
No. of scripts with network deviations over time:
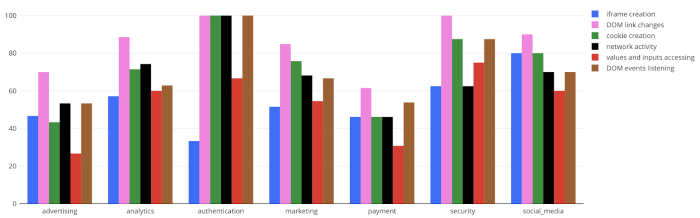
In addition, many vendor scripts seem to add different actions and alter its behaviour from time to time. We are identifying on a daily basis marketing, advertising and other services which started implementing new behavior such as accessing sensitive PII (including credit card values!), creating network activities to outbound destinations and altering DOM elements found on the website.
High portion of third party vectors is prone to exploitation of sensitive PII and has ongoing network contact with various third party domains
When observing across the different vectors of vendors (analytics / marketing / advertising etc.) behavior and actions, we can immediately identify several interesting patterns:
- High portion of scripts which belong to marketing, social media, advertising and analytics vendors have ongoing contact with various network destinations (50-70% out of the monitored vendors), while accessing different user inputs on the website, some of which contain sensitive PII.
- In addition, many of these vendors also create cookies on the user’s local storage for monitoring and targeting purposes. These cookies can potentially contain sensitive information, which we’ve witnessed occurring on some vendors; this isn’t the best practice of holding sensitive information in the GDPR and privacy awareness era.
- It seems that social media vendors utilize iframe creation the most out of all different vectors, around 80% of the monitored vendors. This is not a surprise, as different social media vendors could require a separate authentication process on an external iframe. However, in some cases the iframe is created on sensitive pages as well (Checkout and Authentication pages). This raises concerns regarding sensitive information leakage on these web pages.
Third party libraries and scripts are behaving differently on different websites
Therefore you can never trust a vendor’s behavior even though it is behaving as you would expect on other websites.
For example, even when observing some popular vendor (Google Maps script) attached below – we can see a significant difference in utilization of actions per website. We can identify this script is placing event listeners on various DOM elements and accessing some input elements’ values across part of the websites, while on other websites this activity is not implemented at all.
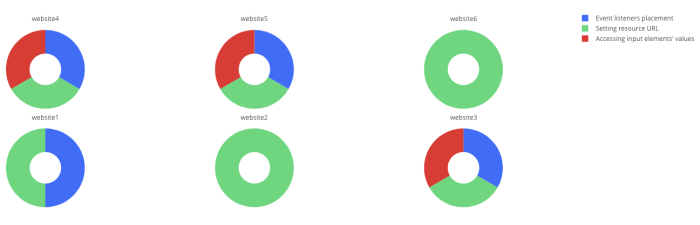
Taking another example – a popular marketing vendor (Hotjar), also seems to behave differently across different websites, implementing various network activities and creating iFrames only on part of the monitored websites:
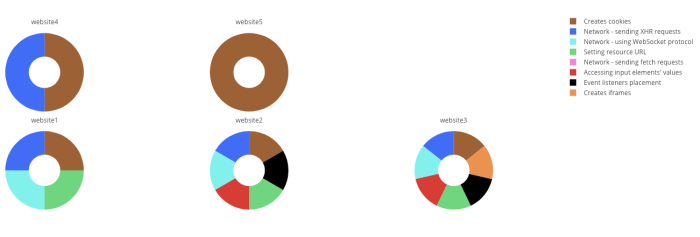
This difference between websites can also evolve as a result of the script’s / vendor’s decision to implement or not to implement a specific behavior. However, the website owner is completely blind at noticing any such behavior change that may actually occur on his or her website.
Conclusion:
After looking at the constantly changing behavior of third party vendors found on industry leading websites across all tiers, we can say for a fact that this is an evolution of modern web development. There is no escape from having these behaviour changes if you want your website to be fully functional and updated at all times.
However, If you want to be fully protected and be able to monitor third party vendors and libraries found on your website, which are a must in these modern days, you should utilize a service which enables ongoing monitoring and visibility into these scripts and their ongoing changing behavior.