Key Account Takeover Protection Capabilities
HUMAN Sightline offers powerful capabilities to block credential stuffing and brute forcing at login, provide deep credential intelligence, and continuously evaluate activities within accounts for fraud.

Defense-in-depth Across Full User Sessions
Protect against account takeovers at every stage of the user journey, pre-, at, and post-login, whether carried out by bots, humans, or AI.
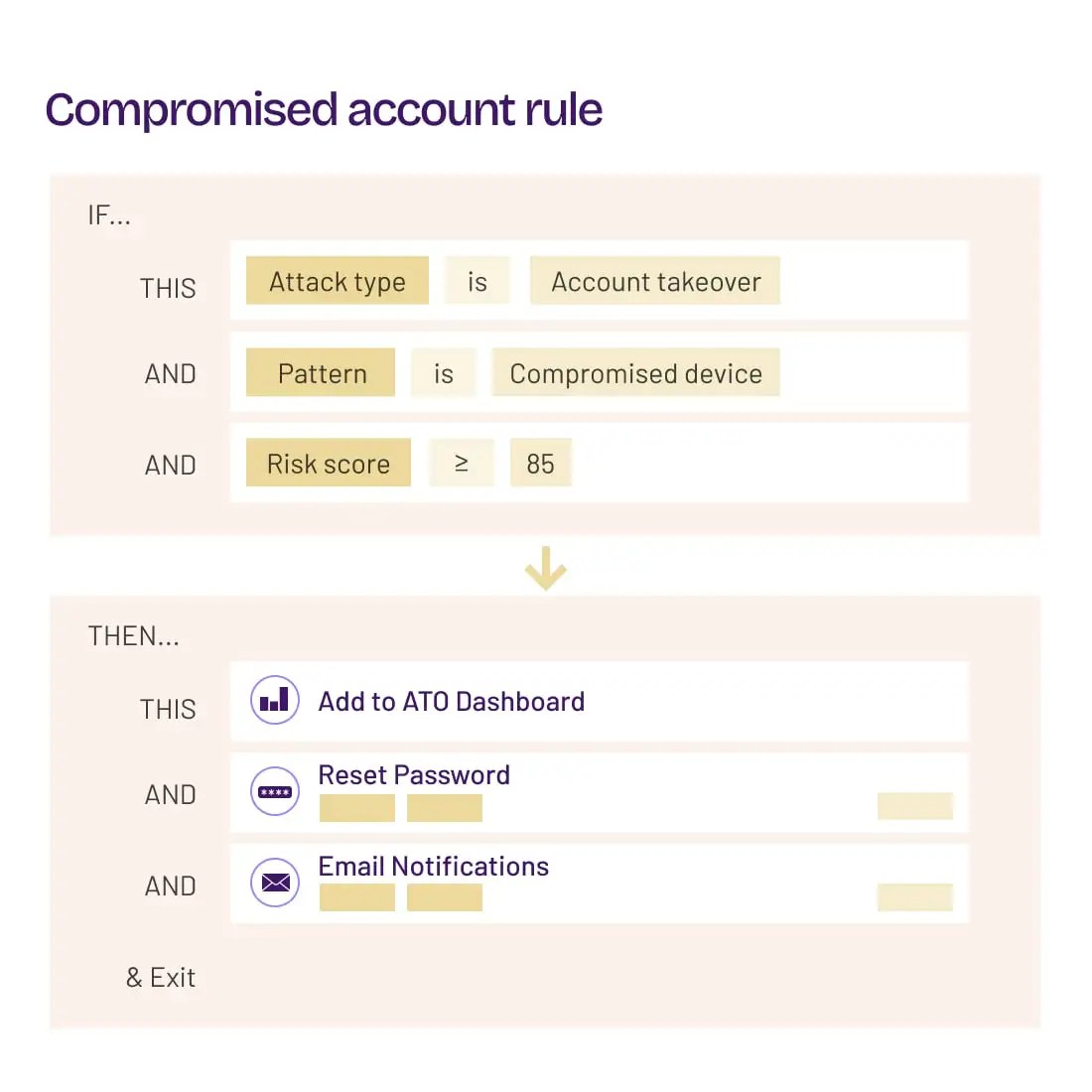
Build Custom Rules and Responses
Easily create multi-criteria rules and responses that automatically trigger when conditions are met. Actions can be custom-built via API to interface directly with internal systems.
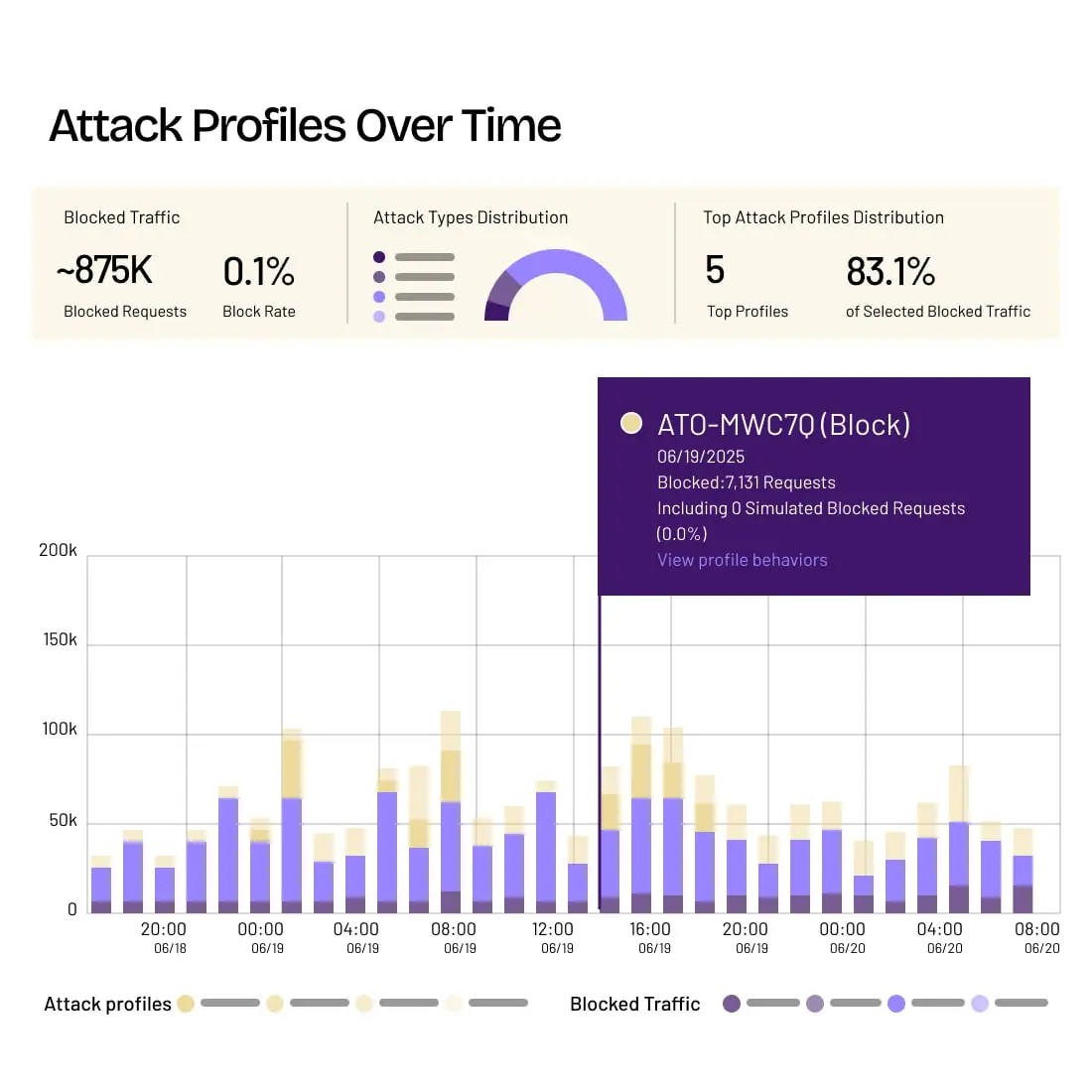
Granular Insight Accelerates Investigations
Pinpoint distinct bot actions, characteristics, and changing behaviors, and uncover hidden patterns, account fraud networks, and evolving risks.
Protecting Customers from Evolving Account Takeover Risks
HUMAN is trusted by global organizations across industries to secure their websites and applications from sophisticated account takeover attacks.
Threat Intelligence:
The HUMAN Element
The Satori Threat Intelligence Team uncovers, analyzes, and disrupts cyberthreats and fraud schemes that undermine trust across the digital landscape, delivering cutting-edge research that strengthens protection for customers and thwarts bad actors for a safer internet.
Explore Satori
Protect Against Account Takeovers with HUMAN
Protect user accounts from automated and human-led fraud and abuse with HUMAN Sightline.
Learn More
FAQ
What is account takeover fraud?
Account takeover fraud happens when cybercriminals gain unauthorized access to legitimate user accounts, often by using stolen credentials, to steal funds, access personal information, or commit further fraud. This type of attack is damaging to consumers and also businesses that face increased fraud losses, operational costs, and reputational harm. Strong account takeover prevention is essential to stopping these threats before they escalate.
What types of fraud and abuse are consequences of account takeover attacks?
HUMAN goes beyond blocking malicious logins by continuously evaluating user behavior throughout the session. If an attacker successfully accesses an account using valid credentials, HUMAN monitors in-session signals – such as unusual navigation paths, rapid changes to account settings, or high-risk transactional behavior – to detect activity that deviates from legitimate user patterns.
When suspicious behavior is identified, HUMAN’s account takeover protection surfaces clear insights that help security teams understand what happened and what the attacker attempted to do. These insights accelerate the investigation process and support faster remediation, such as resetting credentials, revoking tokens, or restoring affected account changes. By combining real-time detection with post-compromise visibility, HUMAN enables organizations to respond quickly and minimize the impact of account takeover fraud.
How do you prevent account takeover?
Effective account takeover prevention involves real-time detection of suspicious login behaviors, behavioral analysis, device fingerprinting, and multi-layered security controls. HUMAN’s solution monitors for anomalies, including rapid login attempts, unusual geolocations, or impossible travel patterns, and blocks takeover attempts without adding unnecessary friction for legitimate users.
Methods For Prevention of an Account Takeover:
- Adaptive Challenges: Trigger CAPTCHA or step-up MFA when suspicious login activity or anomalous user behavior is detected, adding friction only when risk is elevated.
- Login Throttling: Automatically slow, rate-limit, or temporarily lock accounts after repeated failed login attempts to prevent brute force and credential stuffing attacks.
How do you detect account takeovers?
Detecting account takeovers requires more than traditional login monitoring. HUMAN uses behavioral biometrics, machine learning, and advanced ATO prevention technology to establish behavioral baselines—such as login velocity, geographic anomalies, device fingerprint drift, and session behavior, to identify subtle signs of unauthorized access. By analyzing deviations from normal user activity, session hijacking attempts, and rapid credential stuffing in real time, HUMAN surfaces high-risk patterns early, helping stop account takeovers before damage occurs.
How does HUMAN stop account takeovers?
HUMAN stops account takeovers by identifying and blocking the automation and credential abuse that power these attacks. Our account takeover prevention solution uses advanced algorithms to distinguish real users from bots or fraudsters, preventing unauthorized access in real time while ensuring genuine customers continue to experience seamless service.
What other types of cyber attacks can HUMAN prevent?
In addition to account takeover protection, HUMAN helps organizations defend against a broad spectrum of automated threats including scraping, fake account creation, transaction fraud, and client-side attacks. Our multi-layered approach protects businesses across web, mobile, and API environments, ensuring security without compromising performance.
How do account takeover attacks operate?
Attackers harvest stolen credentials either through data breaches, phishing, or underground marketplaces. They then deploy automated bots to rapidly test these credentials across login pages – a tactic known as credential stuffing. Because many users reuse passwords across services, attackers scale this process across multiple high-value sites, making it difficult for basic defenses to keep up.
What can end users do to reduce ATO risk?
While businesses shoulder most of the responsibility for securing their applications, end-user behavior plays a meaningful role in reducing account takeover risk. Users should create unique, strong passwords for each account to prevent cross-site credential reuse – one of the primary drivers of credential stuffing attacks. Enabling multi-factor authentication (MFA) adds an additional layer of verification that blocks unauthorized access even if a password is exposed. Users should also stay alert to phishing attempts, which remain a common method for stealing login credentials in the first place. Taken together, these hygiene practices help limit attackers’ ability to leverage stolen credentials at scale.
Request a Demo