Full Lifecycle Fraud Management
Protect against fraud by bots, humans, and AI agents and enable trusted interactions across the entire customer journey—from first touch to loyal user.
Secure Your Customer Journey
Build trust, protect revenue, and preserve user experience across the entire lifecycle of bot attacks, AI agent risks, and human-led fraud.


Optimize Your Business Goals
Reduce fraud and boost revenue with the perfect blend of appropriate friction and mitigation actions.
Accelerate Threat Response
Investigate threat networks and attacker tactics, then respond faster with AI-enhanced investigation tools.
Streamline Security Workflows
Customize mitigation actions and allow trusted actions with easy integrations, user-defined responses, and application-specific data.
Cyberfraud Defenses and AI Agent Governance
HUMAN Sightline Cyberfraud Defense uses advanced machine learning, behavioral analysis, and intelligent fingerprinting to fight against malicious bot attacks, human-led fraud, and agentic risks.
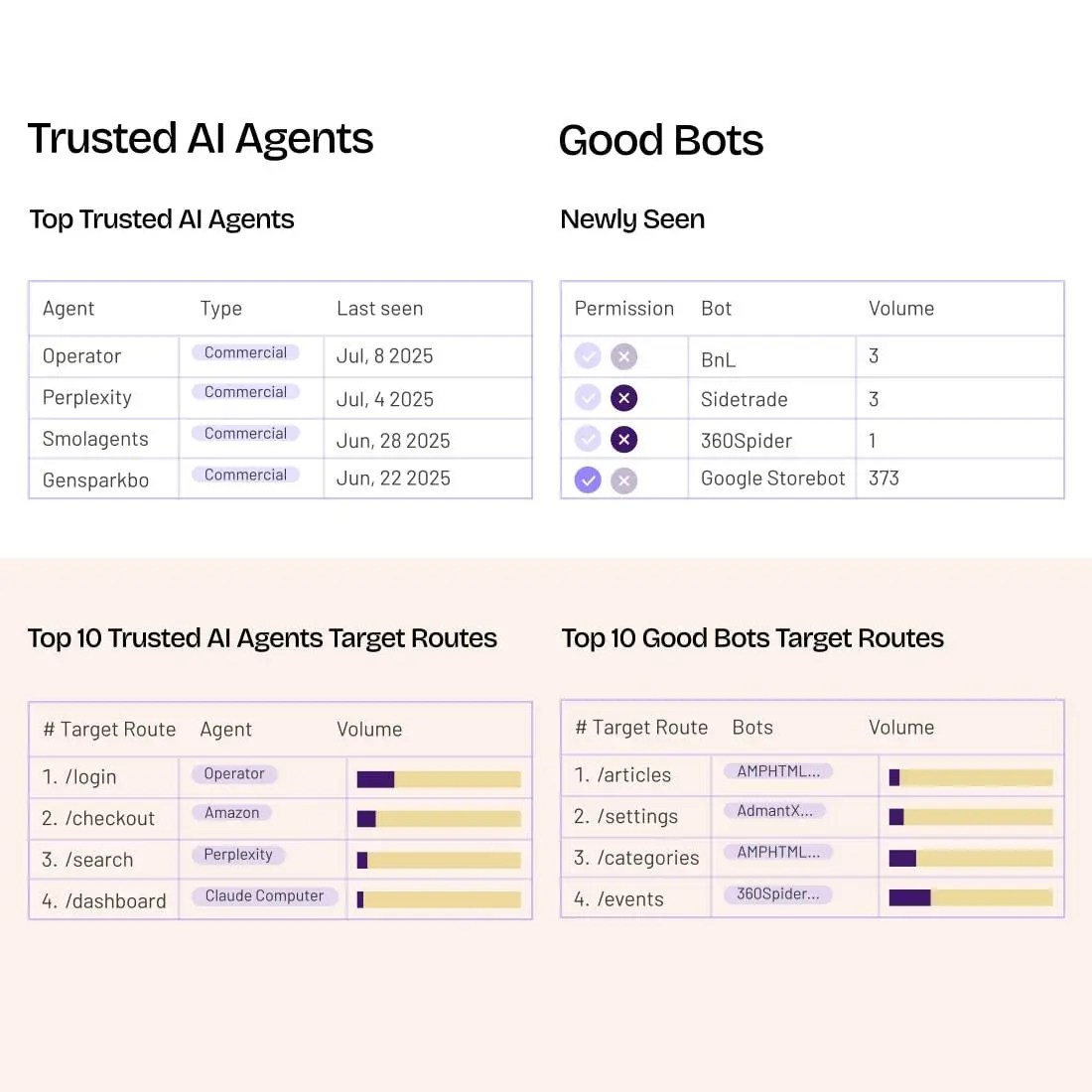
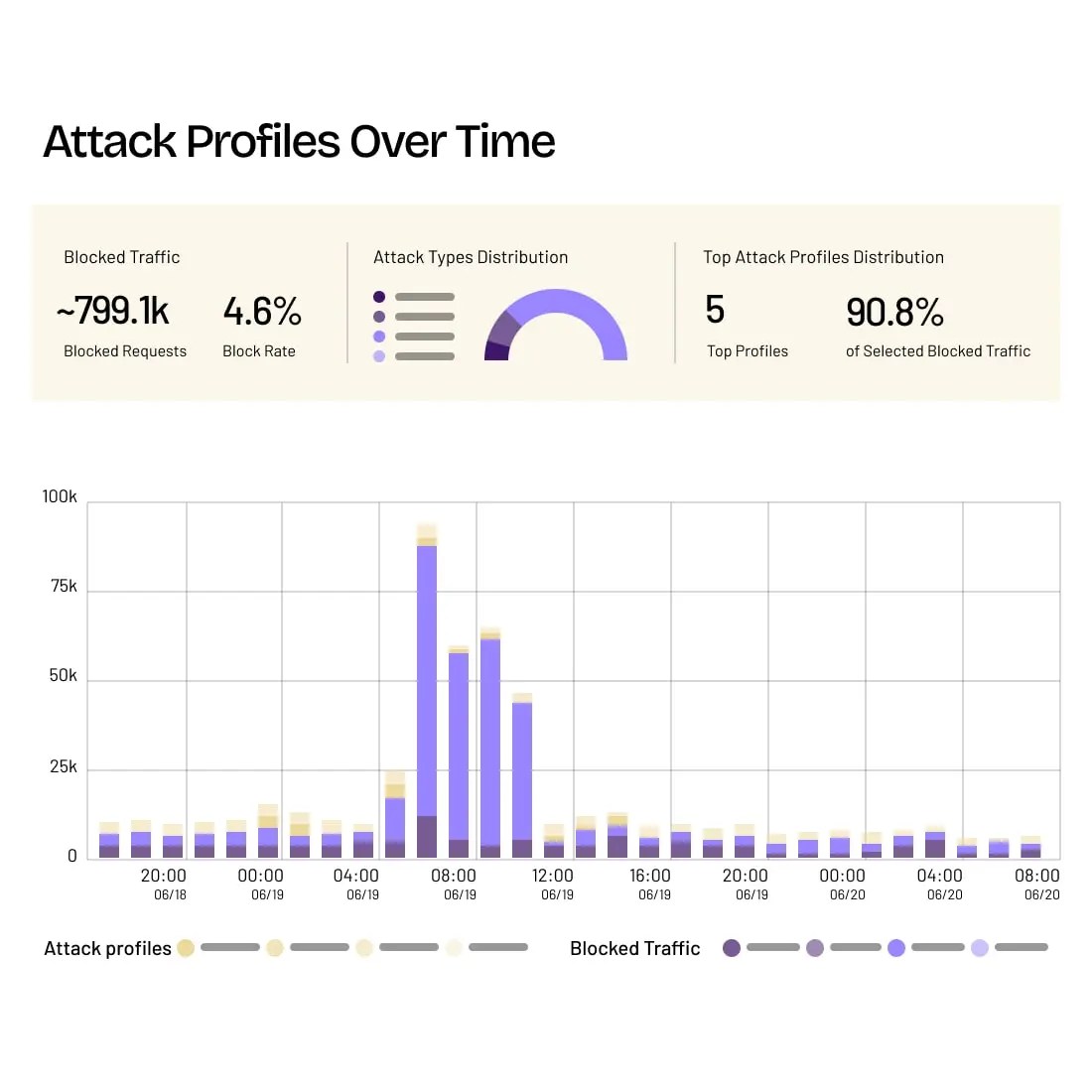
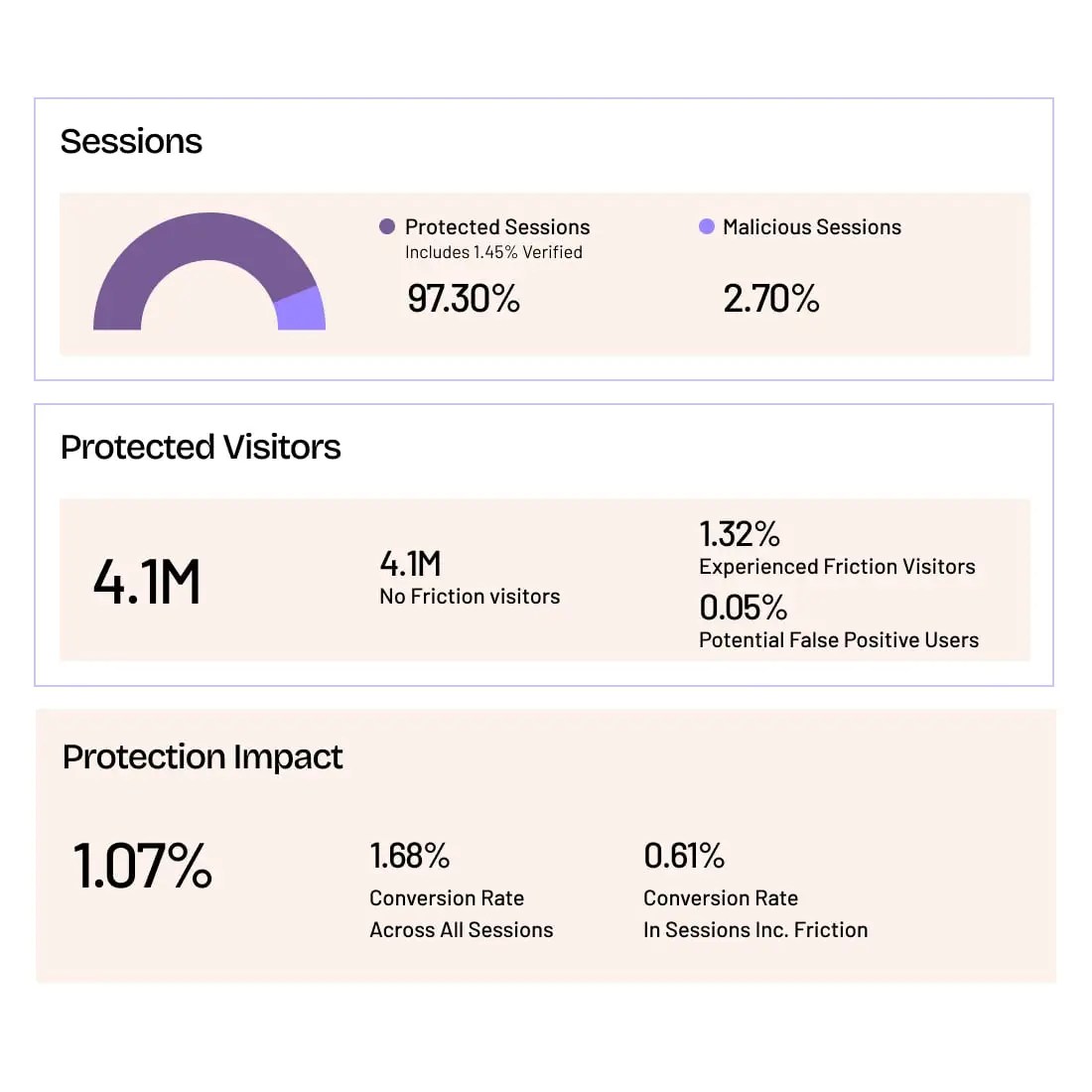
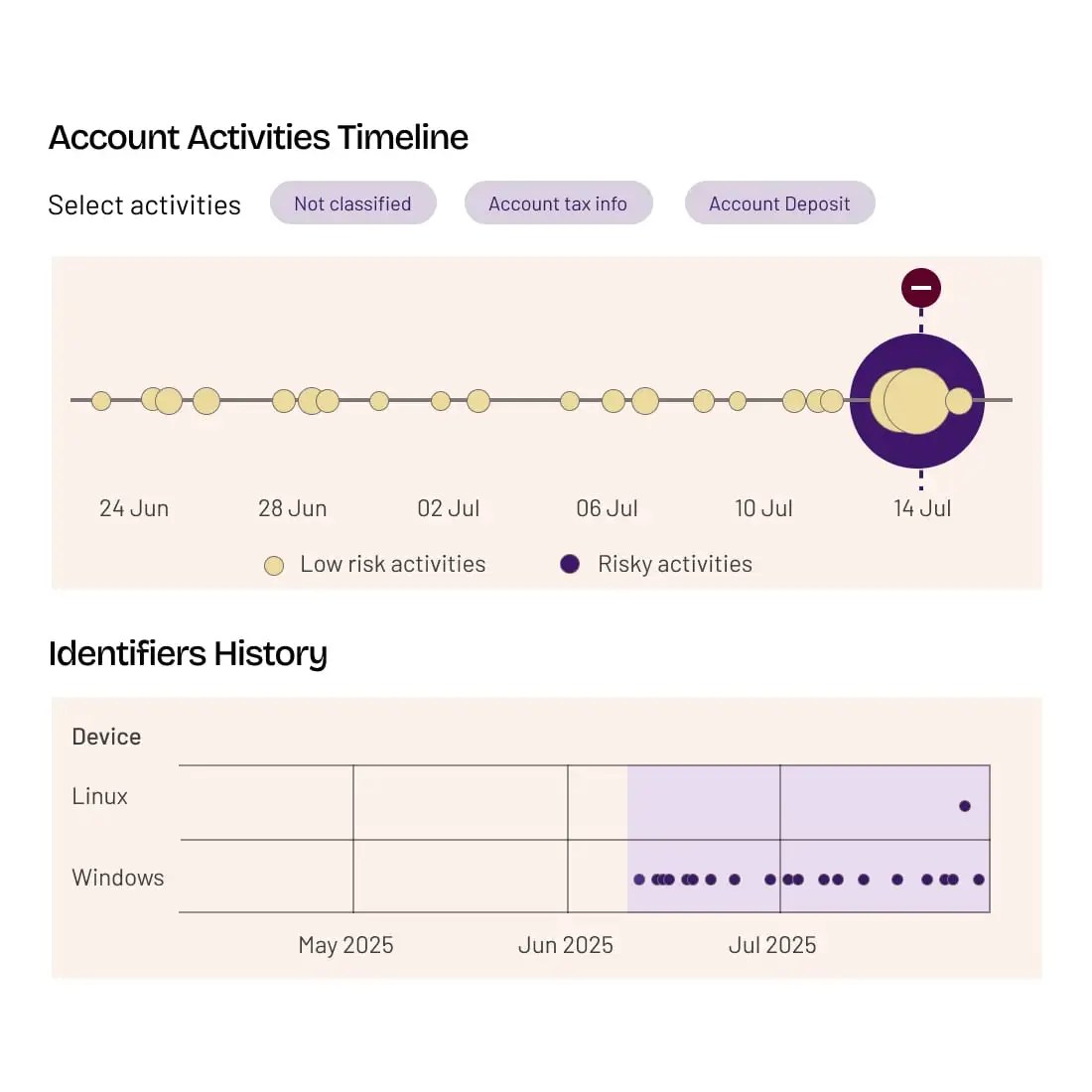
Detect, Mitigate, and Investigate Fraud
Manage good and bad bots, as well as real and fraudulent human traffic, using multi-method detection, customizable mitigation, and deep investigative tools that give you a clear line of sight into what’s happening in your apps and APIs—at every stage of user interaction.
- High-Fidelity Decisioning
- Mitigation and Governance
- Reporting and Investigation
- Adaptive Learning and Feedback
- High-Fidelity Decisioning
High-Fidelity Decisioning
Layered Protection
Continuously analyze and correlate session activity across each authentication stage, rather than looking at individual requests and single methods at disparate interaction points, such as login or checkout.
Adaptive Learning
Layered AI models continuously learn from each detection and mitigation event to automatically detect and react to specific threat adaptations.
- Mitigation and Governance
- Reporting and Investigation
- Adaptive Learning and Feedback
Security that Optimizes Your Business Goals


Not only has HUMAN been invaluable at stopping automated bot attacks and helping us improve server performance, but it has also provided significant benefit to my security team, enabling them to spend far less time dealing with malicious bots and instead focus on other business critical areas.
Richard Spencer CIO, Belk
215%
Increase in attempted ATO attacks on travel/hospitality businesses since 2023
800k
Fake accounts flagged per customer in 2024
We have built a very strong feedback loop with the HUMAN team that allows us to have a tailored proactive approach to protecting our website and our customers from a constantly changing threat landscape.
Senior Director of E-commerce, Hibbett Sports
Scraping Attacks on Streaming and Media Businesses

Threat Intelligence:
The HUMAN Element
The Satori Threat Intelligence and Research Team uncovers, analyzes, and disrupts cyberthreats and fraud schemes that undermine trust across the digital landscape, delivering cutting-edge research that strengthens protection for customers and thwarts bad actors for a safer internet.
Explore Satori
See Cyberfraud Defense in Action