Secure Your Online Accounts With HUMAN
Read time: 3 minutesAlexander Gardner
Have you ever received an odd email with a phishy link? Perhaps it appeared to come from a trusted friend, or maybe it was someone on social media you’ve never met before. Either way, your gut is telling you the sender isn’t who they say they are. And now HUMAN can prove it.
Sending phishy emails is just one way that bad actors commit account fraud. (Check out this article for a more detailed list.) There are two ways that bad actors use accounts to commit fraud:
- Take over existing user’s accounts, using techniques such as credential stuffing, brute forcing, malware, phishing, session hijacking, and social engineering to beat login defenses. Once they gain access to a legitimate account, they can drain the account balance, steal stored payment data and PII, and commit other types of fraud.
- Create fake accounts to extract value from organizations and abuse their services. Examples include exploiting promotional activities such as free trials, distributing malware or posting negative reviews to disparage competitors.
Whatever the flavor, cybercriminals are betting that they won’t be caught at login. If they’re able to successfully take over a user’s account or create a fake account, they may then have free rein to take action within the account.
Fill the post-login security gap
Focusing account security at login and at point of transaction leaves a significant blind spot for users’ activity post-login, but pre-transaction. And cybercriminals are taking advantage of this.
A fake or compromised account is the perfect way for bad actors to distribute spam or malware, reroute shipping orders to their own address, take advantage of promotional offers, access gated content, or capture users’ PII — all without tripping alarm bells.
HUMAN Account Fraud Defense monitors all post-login activity taken in an account, catching suspicious and risky behavior that at-login solutions cannot see. It also enables earlier intervention than solutions that operate at the point of transaction because it detects malicious behavior earlier in the process.
Neutralize fake and compromised accounts
Account Fraud Defense neutralizes compromised and fake accounts by delivering continuous post-login monitoring and risk assessment. The solution looks at all activity taken in an account and assesses the individual actions, cross-referencing with multiple variables (e.g. is this a new device login? Is it a new geographical location?) to assign an evolving risk score to accounts.
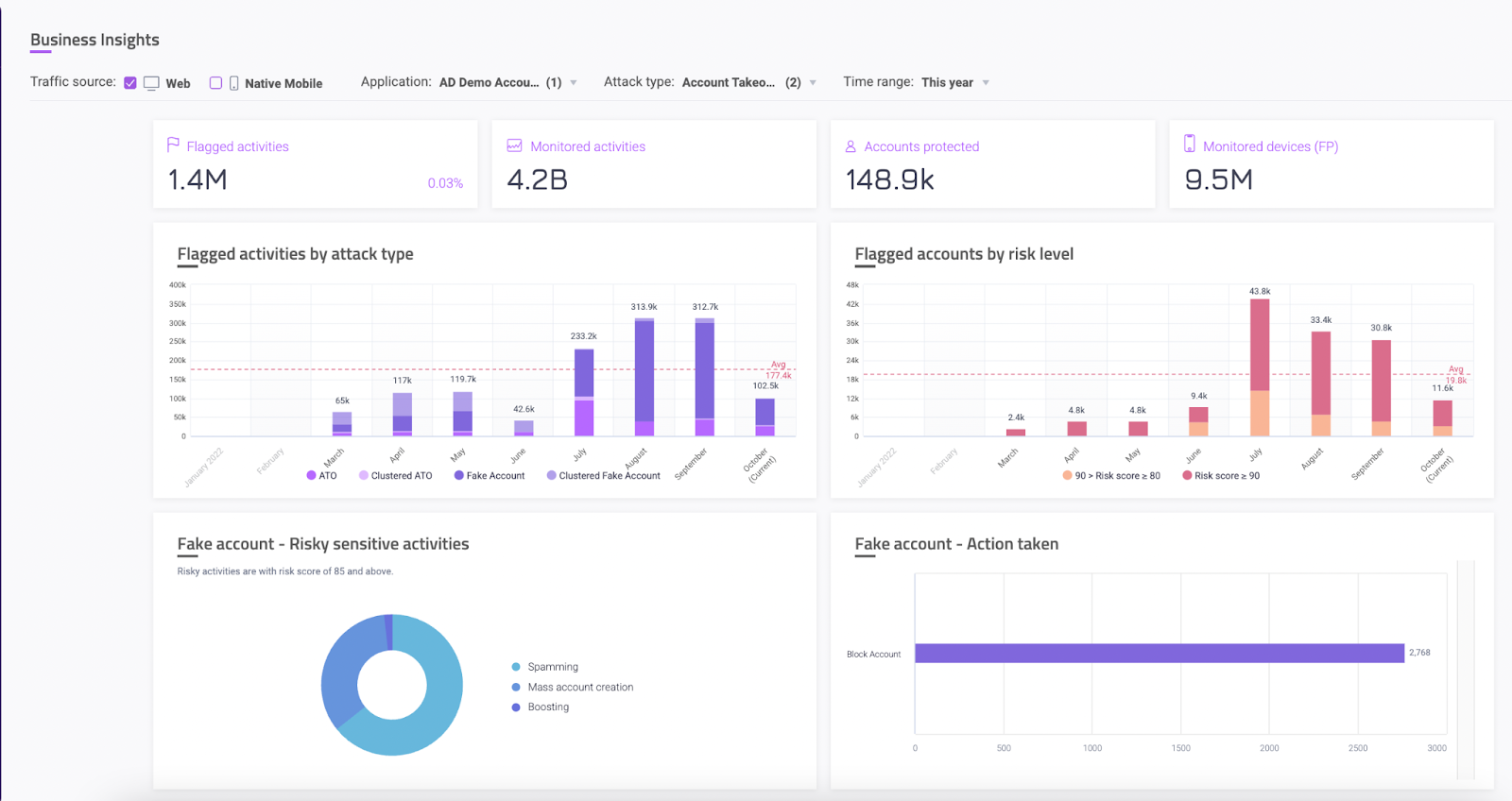
When a risk threshold is passed, the solution automatically takes actions to protect the account and user, without the need for manual intervention. These actions are fully customizable and integrated with your organization’s workflow. Examples include forcing a password reset, triggering MFA, or flagging the account for review.
With the Account Fraud Defense dashboard, fraud, compliance, trust and safety and other teams can quickly ascertain what triggered an incident and see what action was taken to neutralize it. Sharing key information is easy with a selection of pre-built reports, as well as the ability to create custom reports tailored to your organization’s needs.