The White Ops Threat Intelligence team recently identified 100+ malicious apps, with more than 4.6 million downloads, performing ad fraud. All of the apps use a common code package White Ops has dubbed “Soraka” (com.android.sorakalibrary.*):
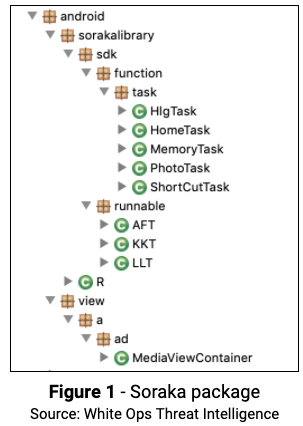
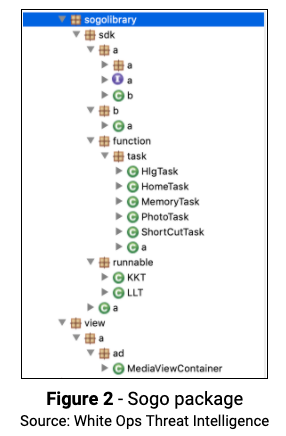
In addition to the Soraka code package, we also discovered, in some of the apps, a variant with similar functionality which we dubbed “Sogo” (com.android.sogolibrary.*):
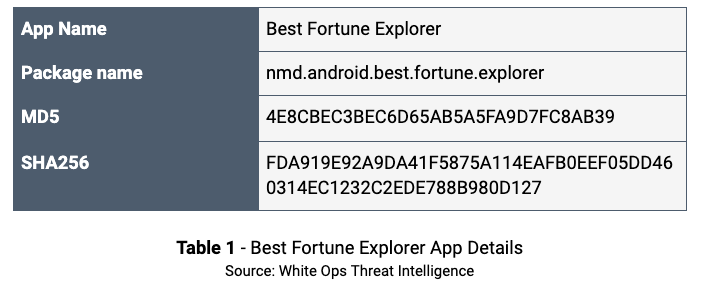
Best Fortune Explorer App
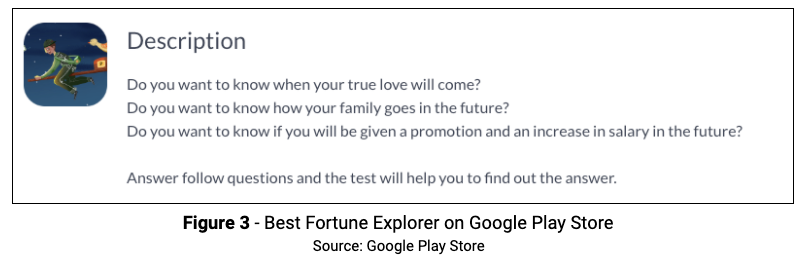
One example of the Soraka package was the “Best Fortune Explorer” app by the publisher JavierGentry80. This app was released on September 9, 2019 and is the only app published by JavierGentry80. Best Fortune Explorer is, as of this writing, available on the Google Play Store and has no Anti-Virus (AV) detections on VirusTotal. This app has more than 170,000 downloads.
Fraud Activity Filters
The apps are using a framework called AppsFlyer for mobile attribution and marketing analytics. The app displays fraudulent ads only if AppsFlyers determines the installation is NOT organic, meaning the install was attributed to a promotional effort by the fraudsters. There are several filters the code checks before a fraudulent ad is shown to the user:
The filtering is likely a mechanism to avoid detection from automated analysis and other services that would install the app ad-hoc and then, most likely, be considered as organic by AppsFlyer.
This mechanism also allows fine-grain control of who (or what) receives the ad fraud, using the controls of ad serving platforms. The apps render out-of-context ads when the filter conditions are appropriate.
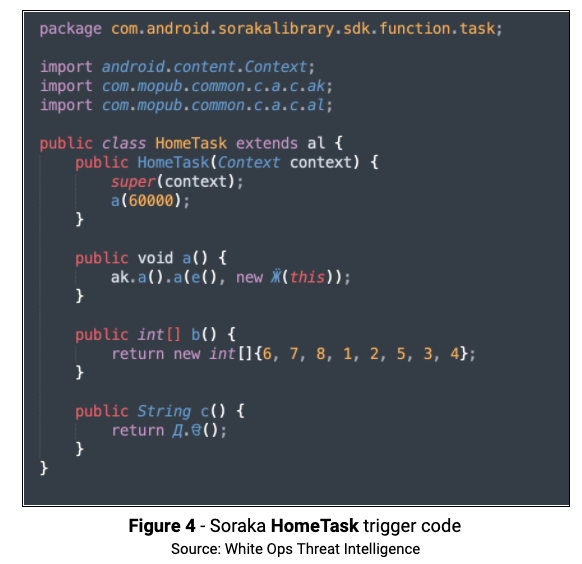
The Soraka package can be found in com.android.sorakalibrary, and utilizes several triggers to make the determination of what to run. As an example, int[ ] b( ) returns an integer array of filters this trigger (pressing the Home button) needs to check before running. The method public String c( ) in HomeTask returns the name of the trigger. All of the trigger classes implement this method, each returning its name. To further obfuscate the code and make analysis more difficult, HomeTask creates a class named with the Cyrillic character Ӝ, which is part of the Udmurt language. The class Ӝ goes to a Mopub method ah where the onAdloaded function is called to start the ad rendering process.
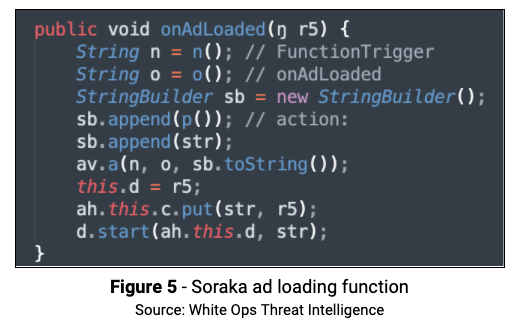
Ad Fraud
White Ops Threat Intelligence identified the following ways the app rendered ad fraud:
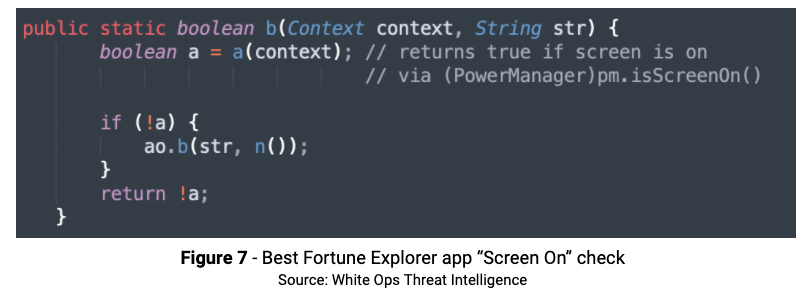
There is also code initiating fraud activity only while the device screen is ON and the host app is NOT on top.
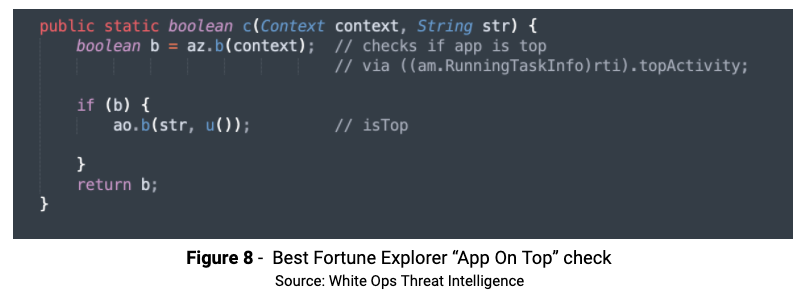
Broadcast Receivers
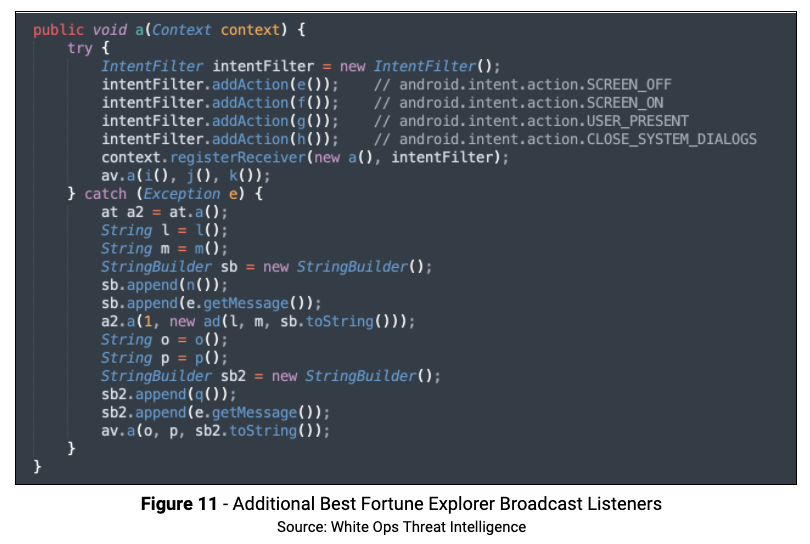
The Best Fortune Explorer app code dynamically registers broadcast listeners for several actions, which is important to detect things like screen state, user presence, and when the home button is pressed.
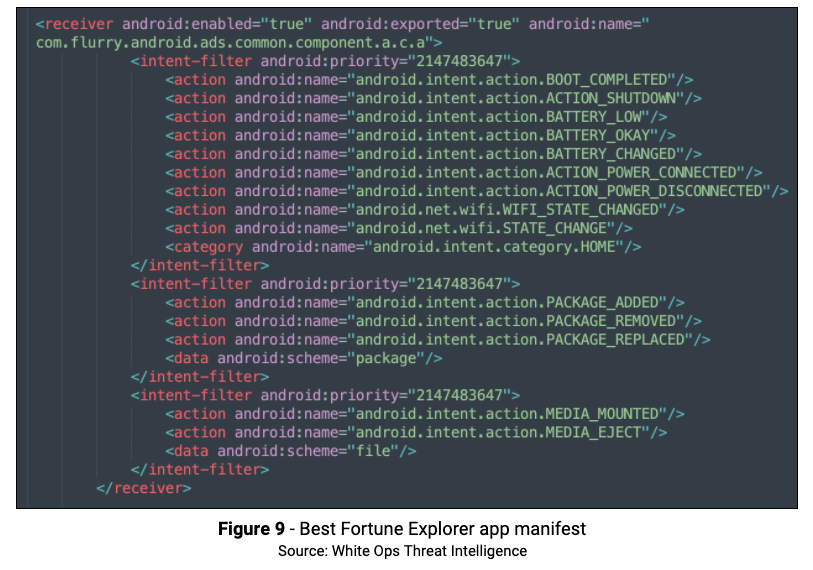
The app manifest lists the broadcast receivers class as com.flurry.android.ads.common.component.a.c.a. where we can see the onReceive function in the figure below.
An additional set of broadcast receivers are located in com.mopub.common.c.a.c. As shown below, these receivers will run when the actions, noted in the code comments, occur.
Persistence
The main Java based persistence mechanisms are initiated by the Java class in com.mopub.common.c.a.c.b, and use imports to start a service. The types of persistences vary. The most common ones are:
Method b will set the alarm mechanism, the intent will start com.flurry.android.ads.common.component.a.d.a which is a service:
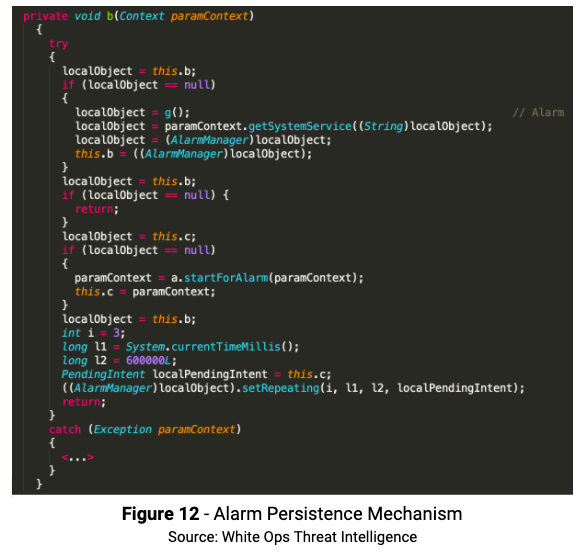
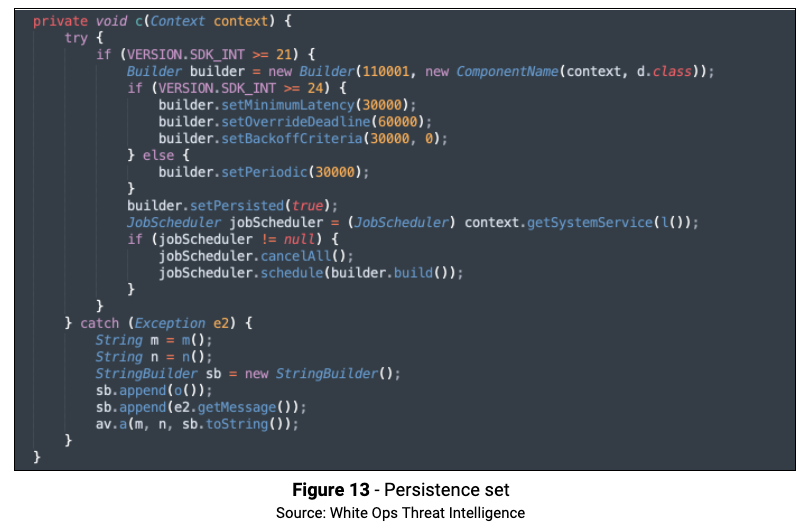
The method c( ) starts a Job that will periodically run com.flurry.android.ads.common.component.a.d.d. If the SDK version is greater than 24, then the Job is set as “Persisted”, which will make it run even after the device restarts.
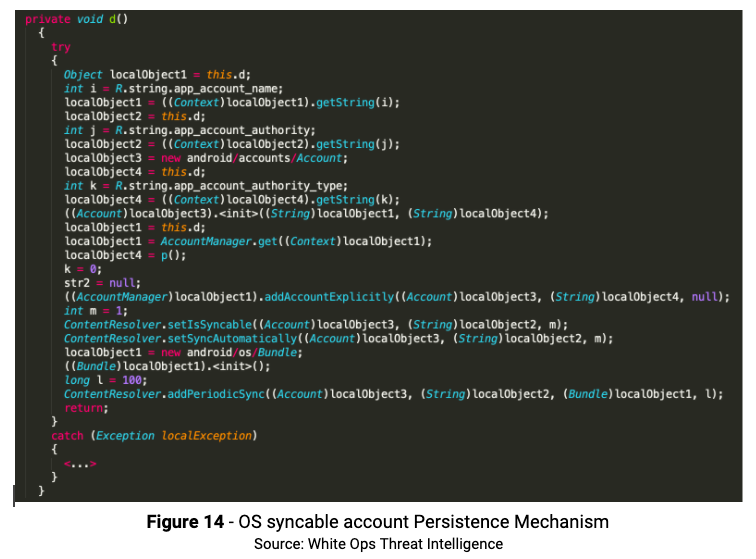
Method d( ) has the ability to create an account in the OS, set it to be “Syncable” and to be automatically synced. The method determines the period for the syncing to 100 seconds as seen below:
The new account created was seen in the device Settings>Accounts.
Besides Java based persistence, this threat also uses Native libraries:
The native function dp (Lollipop library) and dk (KitKat library) enter an infinite loop in which every 10 seconds a set of files are checked for locking. A callback Java function is called, if needed, so the files checked are:
If the app is force closed, then the library detects it and brings it back via the java_callback function.
Wrap Up
The White Ops Threat Intelligence team continues to monitor these packages and will identify any emerging packages. We recommend removal of any apps listed in the Indicators of Compromise section below.
Indicators of Compromise (IoC)
App Packages Using Soraka and/or Related SDKs:
Package Name:
| art.photo.editor.best.hot |
| bedtime.reminder.lite.sleep |
| com.am.i.the.best.friends.hh |
| com.appodeal.test |
| com.beauty.mirror.lite |
| com.bedtimehelper.android |
| com.bkkmaster.android |
| com.calculator.game |
| com.card.life |
| com.cartoon.camera.pro.android |
| com.code.identifier.android |
| com.code.recognizer.android |
| com.color.spy.game |
| com.cute.kittens.puzzlegame.android |
| com.cute.love.test.android |
| com.daily.wonderfull.moment |
| com.dailycostmaster.android |
| com.dangerous.writing.note |
| com.data.securite.data |
| com.days.daysmatter365.android |
| com.days.remind.calendar |
| com.detector.noise.tool |
| com.dodge.emoji.game |
| com.dog.bark.picture.puzzle |
| com.drink.water.remind.you |
| com.ezzz.fan.sleep.noise |
| com.fake.call.girlfriend.prank2019 |
| com.fakecaller.android |
| com.fake.caller.plus |
| com.false.location |
| com.fancy.lovetest.android |
| com.fast.code.scanner.nmd |
| com.filemanagerkilopro.android |
| com.filemanagerupro.android |
| com.filemanageryo.android |
| com.filemanagerzeropro.android |
| com.find.difference.detective.little |
| com.find.you.lover.test |
| com.frame.easy.phone |
| com.frank.video.call.lite |
| com.free.code.scanner.nmd |
| com.free.lucky.prediction.test |
| com.funny.lie.truth.detector |
| com.funny.word.game.english |
| com.game.color.hunter |
| com.ice.survival.berg |
| com.idays.dayscounter.android |
| com.important.days.matter |
| com.instanomo.android |
| com.isleep.cycleclock.android |
| com.led.color.light.rolling |
| com.lite.fake.gps.location |
| com.lovetest.plus.android |
| com.love.yourself.women |
| com.lucky.charm.text |
| com.lucky.destiny.teller |
| com.magnifying.glass.tool |
| com.math.braingame.puzzle.riddle |
| com.math.iq.puzzle.riddle.braingame |
| com.math.puzzles.riddle.braingame |
| com.multiple.scanner.plus.nmd |
| com.my.big.days.counter |
| com.my.constellation.love.work |
| com.my.pocker.mobile.mirror |
| com.nanny.tool.data |
| com.nice.mobile.mirror.hd |
| com.nomophotoeditor.android |
| com.non.stop.writing |
| com.phone.lite.frame |
| com.phone.mirror.pro |
| com.pocker.pro.mobile.mirror |
| com.prank.call.fake.ring |
| com.phonecallmaker.android |
| com.pro.test.noise |
| com.puzzle.cute.dog.android |
| com.scan.code.tool |
| com.simple.days.counter |
| com.sleep.comfortable.sounds |
| com.sleep.in.rain |
| com.sleepassistantool.android |
| com.sleeptimer.android |
| com.smart.scanner.master.nmd |
| com.test.find.your.love |
| com.test.fortune.tester |
| com.test.lover.match |
| com.tiny.scanner.tool.nmd |
| com.wmmaster.android |
| com.word.fun.level.english |
| good.lucky.is.coming.hh |
| mobi.clock.android |
| my.lucky.goddness.today.test |
| newest.android.fake.location.changer |
| nmd.andriod.better.calculator.plus |
| nmd.andriod.mobile.calculator.master |
| nmd.android.best.fortune.explorer |
| nmd.android.better.fortune.signs |
| nmd.android.clam.white.noise |
| nmd.android.fake.incoming.call |
| nmd.android.good.luck.everyday |
| nmd.android.location.faker.master |
| nmd.android.multiple.fortune.test |
| nmd.android.scanner.master.plus |
| nmd.android.test.what.suitable |
| photo.editor.pro.magic |
| pic.art.photo.studio.picture |
| relax.ezzz.sleep.cradle |
| super.lucky.magican.newest |
| test.you.romantic.quize |
| well.sleep.guard.relax |
| your.best.lucky.master.test.new |
| com.ssdk.test |
| bedtime.reminder.lite.sleep |
| com.frank.video.call.lite.pro.prank |
| com.personal.fortune.text |
| com.daily.best.suit.you |
| com.false.call.trick |
